Passwordless, are we there yet? Even though Passwordless means different things to different people, in my interpretation of user initiated password obsolescence I’ve minimised typing passwords as much as possible. In this post I’ll detail how.
Eliminating Password Use in the Enterprise
You don’t need to wait for your organisation to start promoting and urging you to go passwordless. In my experience the majority of larger enterprises have the capabilities already enabled. As an end user you will need a few items to make life seamless and go passwordless yourself.
Enablers to go Passwordless
- A password manager that works across platforms (desktop, browser, mobile)
- personally, I’ve been using 1Password now for many years. I have it installed and use it daily across mobile, web and desktop. Also, via API for DevOps activities.
- FIDO2 Token(s)
- A hardware token supporting WebAuthN CTAP2. There are many available now including the ones I’ve mentioned previously. Personally I’m a fan of YubiKey because of their USB-A, USB-C, Lightning interfaces and now the Bio Series
- Additionally the recent release of their YubiKey SDK for Desktop that allows integration via PowerShell for certificates. These can be used for Certificate Based Authentication (again, no password here with examples in Python and PowerShell).
- Windows Hello capable device(s)
- Either a Windows Hello Webcam or Fingerprint reader. I have a few laptops. The older ones have fingerprint readers, and the later models have Windows Hello capable cameras.
- There is also the option to add external Windows Hello devices
- such as the Lenovo 500 FHD Webcam or the Kensington VeriMark Fingerprint USB Dongle
- Mobile (tablet/phone) with biometrics (e.g., FaceID, Fingerprint)
Azure AD / Microsoft 365 First Login
Late last year (2021) I started with a new employer. I was issued a new managed laptop and was provided my UserID and initial Password all remotely … because 2021. This was the first time I’ve had a company issued device is over 6 years. I decided before I even unboxed it, I was going to experiment with the challenge of only ever typing my corporate identity password once (i.e., that very first login).
My primary goal logging in the first time was to proof-up my profile with additional authentication mechanisms, change my password and never type it again.
Ideally rather than being issued an initial password the new preview feature “Azure Temporary Access Pass” could have been used.
On my newly issued Windows 10 laptop, my first logon and additional authentication methods enrolment process went like this.
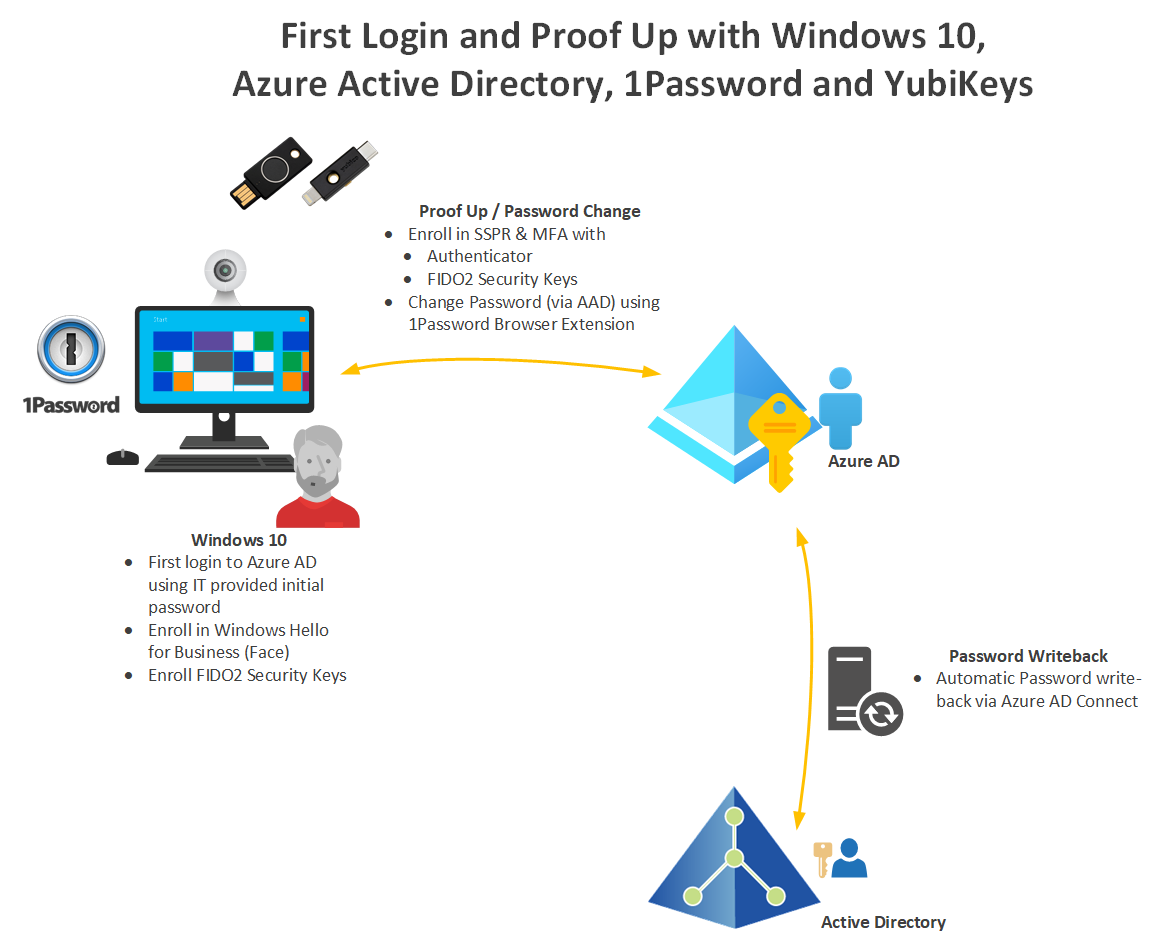
First Login Step by Step
- Entered my Login ID (UPN) and initial Password into the Windows 10 login window
- Azure AD authentication directed me through the proof-up registration process to enrol in Azure AD MFA (Multi Factor Authentication) and SSPR (Self Service Password Reset)
- For MFA I enrolled in Microsoft Authenticator on my iPhone and also enrolled a YubiKey Bio (USB-A) and a YubiKey 5Ci (USB-C and Lightning)
- I use the YubiKey Bio as my primary key as it has my fingerprint enrolled so I don’t need to type a PIN. The second YubiKey is my backup key. It may also serve future use cases around mobile 2FA.
- For MFA I enrolled in Microsoft Authenticator on my iPhone and also enrolled a YubiKey Bio (USB-A) and a YubiKey 5Ci (USB-C and Lightning)
- Then I installed the 1Password Browser Extension that would enable me to automatically populate authentication dialogs. I enabled Windows Hello for 1Password authentication (more on this below)
- Next, I went to https://myaccount.microsoft.com/ and changed my password using 1Password. As I had previously via my phone entered my initial password (copy and paste from the IT notification) I didn’t need to type it in. 1Password generated a new, unique and long random new password and automatically populated the two dialog boxes to set my new password. And it saved the new password into my 1Password vault.
- Azure AD Connect synchronized my password back to Active Directory from Azure AD.
- Finally, on Windows 10 I enrolled in Windows Hello with my laptops’ Windows Hello capable webcam, and I also enrolled the YubiKey Bio and YubiKey 5Ci.
Challenge Check
So far, I had typed my new corporate identity account password once. Just for that initial login. I had previous created an entry for the account in 1Password and used copy and paste from the notification that gave me the initial password. BUT the one omission from the above process is BitLocker. That important by annoyingly independent and isolated BIOS and OS driven hard-drive encryption. There is no way around that, but that password is also in 1Password as is only required on restart. And that is rare and usually after patch updates.
Mobile Enrolment & Usage
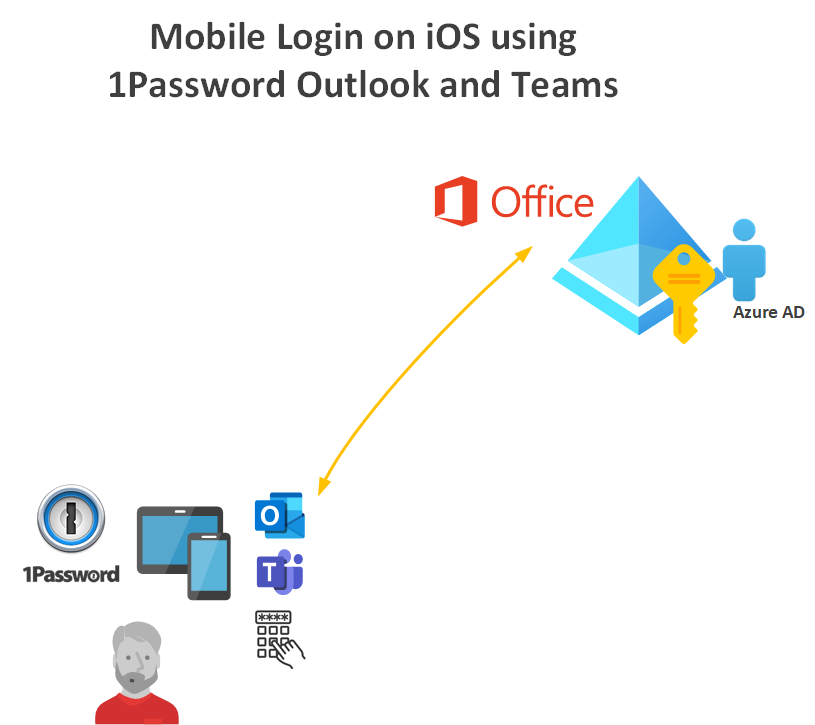
Now that my Windows 10 laptop and my Azure Active Directory (and subsequently Active Directory) accounts were enrolled and secured it was time to configure my mobile phone to allow access to my Microsoft Exchange Online mailbox (via Outlook for iOS) and Teams for meetings and chat.
I already had 1Password on my mobile phone, so knew that it had the new password for my Azure AD Account. Adding my new Exchange Inbox to Outlook on mobile and signing into Teams triggered the MDM enrolment process. I simply had to set a PIN for the apps even though authentication will be with FaceID. Naturally I stored the PIN in 1Password. The PIN is used as a fallback for biometrics (if FaceID fails). Needless to say, I’ve never entered the PIN.
What does daily use look like?
Each day I unlock my laptop using Windows Hello and my laptops webcam. Each time I walk away from my laptop I lock it using Win + L or it will auto-lock when my mobile phones’ Bluetooth connection disconnects. The laptop auto-locks using the Windows 10 Dynamic Lock feature (see Account Protection settings below). Each month when prompted to change my password I change it using Azure AD change password (under My Account in Azure AD). I do it this way as it uses my browser with the 1Password extension, so I don’t need to know or type the current password to set a new one. The new one is also auto generated and populated by 1Password.
If I’m logging into an application that isn’t directly integrated with Azure AD for SSO and I’m presented the Azure AD login window I use the Sign in with Windows Hello or a security key option. As a fallback I could use the FIDO2 token, but the Windows Hello camera fires up and I’m in.
When using my mobile phone with Outlook or Teams these applications auto-unlock using the iPhone FaceID.
Account Protection
In addition to Account Protection on Windows 10 and above I recommend enabling Dynamic Lock. By pairing your mobile phone using Bluetooth to your Windows 10/11 machine you can then enable Dynamic Lock. This setting automatically locks your PC when you move away from your PC with your mobile phone. You should of course use the Win + L shortcut to lock your PC, but if you forget this is a good fallback. Enable under Windows Security => Account protection.
Also located under Account Protection is where you setup Windows Hello as I did after my first sign-in.

Summary
Whilst not completely passwordless in the strictest sense, I haven’t typed my Azure AD account password in since the very first login. In the strictest sense a temporary access pass could have been issued and phish proof methods of authentication setup and solely used. Technically there is a password on my account and my password manager knows what it is. But through biometrics it never gets used. There is also the BitLocker password on the laptop that once a month needs to be typed after Windows restarting.
On my phone everything is FaceID driven (phone unlock, MDM protected application opening, and unlocking authenticator). On my laptop everything is Windows Hello or biometric token driven. Other than using 1Password to retrieve the account password to change it each month, it never gets retrieved.
From a user driven user experience it is very passwordless. I don’t know what my password is and will never have to type it.