Evaluation criteria for product selection can be a difficult process, especially for items that are rarely purchased. We’ve become accustomed to working out what we want from daily use items such as laptops, and mobile phones which does make that process easier when we refresh them every few years. However, choosing a hardware security token is maybe something you haven’t ever had to do.
So how do I choose a Hardware Security Token? This post outlines some selection criteria I’ve recently used to assist others with answering “Which Hardware Security Token do I need?” with a view to using the tokens for Azure Active Directory Passwordless authentication along with support for other multi-factor scenarios.
In this post I cover;
- Hardware Security Token Product Selection
- Enrolling / Configuring a FIDO2 Hardware Token
- Azure AD FIDO2 Token Enrolment
- Passwordless Authentication to Windows 10
- Enable an Azure AD Tenant for FIDO2 Passwordless Authentication
- Joining a Windows 10 machine to Azure Active Directory
Product Selection – Hardware Security Token Protocols & Interfaces
Hardware Security Tokens come from numerous vendors. Until recently (late 2019) there was only two manufacturers (Feitian and Yubico) that had a hardware token that supported FIDO2 as the FIDO2 standard was only recently endorsed. Thankfully that has now changed, and our options are increasing. That though also compounds the problem. Which vendor do I choose and which of their hardware token products are right for me? Here are some criteria to consider;
- What scenarios will you be using the security token for? What protocols do we need?
- As per the title of this post, our primary requirement is Passwordless Authentication to Azure Active Directory. The first requirement therefore is FIDO2.
- But what about also using a hardware security token to secure your personal email account (e.g. GMail, Outlook), your social accounts such as Facebook, Twitter, Instagram…..? Those services currently commonly use FIDO U2F. The second requirement may therefore be FIDO U2F.
- What about also using the hardware security token for corporate environment access. Often TOTP (time one-time-password) second factor authentication is used. Those rolling 6 digits that change every 30 or 60 seconds used during authentication. Or even Smart Card (PIV) certificate support. A third requirement may then be TOTP and or Smart Card PIV support.
- What USB ports are on the computers you use?
- USB-A and or USB-C?
- What about options to use a hardware security token with mobile? NFC for mobile/tablets (predominantly Android support for NFC).
- For Apple iOS, Yubico does now have a token that supports the lightening connector (but keep in mind that apps on your mobile need to also support hardware tokens. App support is currently limited but is growing).
- Finally, a bio-metric or PIN based hardware security token?
- The advantage of bio-metric is you don’t need to actively remember or input a PIN as part of the authentication process. You just use your fingerprint.
- For tokens without a bio-metric sensor you will need to use a PIN as well as usually a capacitive touch sensor on the key.
In late 2019 there were minimal hardware security tokens that were available that supported multiple protocols (FIDO U2F, FIDO2, TOTP etc AND were bio-metric). Current options are Feitian BioPass, eWBM Goldengate series (FIDO2 and FIDO U2F only) and Yubico indicating they have a Yubikey Bio coming soon. Keep abreast of announcements on the Find Biometrics FIDO2 page here.
Anything else?
Whilst the options above cover what are you going to use the hardware token for, there are other things you should also consider, especially if you are looking to purchase numerous keys for an organisation;
- physical materials that the hardware token is made of
- will the hardware token stand up to the treatment it will get in your or your user’s environments?
- where the token is manufactured
- for some organisations this is a deal breaker, if it isn’t made locally or from a trusted source. Often manufacturers are keen to point out if their devices are NOT manufactured in China
- key management
- this is more for an organisation to consider; Enrolment and assignment of tokens to individuals. Do the hardware tokens have a serial number, and can we verify who has what token (more for TOTP use cases)
- key availability
- if you are only buying for yourself (buy 2 so you have two enrolled, one for daily use and one as a backup stored in a secure location) this probably isn’t a major concern. But if you are buying thousands you will need to evaluate availability and lead times.
- cost
- this is relative to your criteria and how many you are buying. But hardware tokens do vary in cost, and if you are buying for an organisation it will affect your decision making, especially planning for lost tokens, faulty tokens and token turnover
- user experience
- this is one of the most important, but in the context of passwordless authentication it really boils down to either using a PIN or a fingerprint scan as part of the authentication process. (See Passwordless Authentication to Windows 10 below)
Confused? A recommendation
My recommendation is, as a minimum select a;
- hardware token that has bio-metric with at least FIDO2 and FIDO U2F protocol support and either a USB-A or USB-C interface (depending on what you will be plugging it into)
- current options therefore are Feitian BioPass, eWBM Goldengate
Enrolling/Configuring a FIDO2 Token
This is very dependent on the manufacturer and how they have designed and integrated their hardware tokens. Ideally you are looking for full Windows 10 integration in order to not have additional driver and software dependencies to configure/enrol with the key. Before following manufacturer instructions to download additional software go to Windows Settings => Accounts => Sign-in options
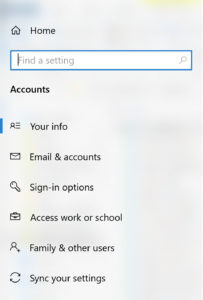
Select Security Key

Select Manage
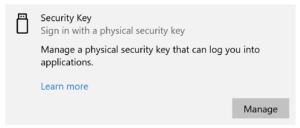
Touch the Security Key
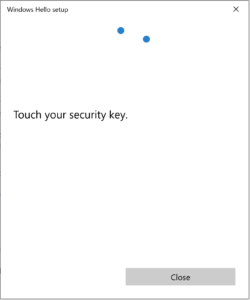
If you got this far, you are on a recent build of Windows 10 (Windows 10 Build 18298 (19H1) or above) and you can manage the key and enrol your finger print(s), set a PIN and reset the key. If you didn’t get this far successfully you will need to install drivers and key management software from the vendor or update your Windows 10 OS.
For bio-metric keys you should see the Security Key Fingerprint options (right image below). Either add additional fingerprints if a user is already enrolled, or enrol fingerprint(s). For both bio and capacitive touch keys you can manage the PIN and reset the key.
Azure AD FIDO2 Token Enrolment User Experience
Registering a FIDO2 token for Azure AD Passwordless Authentication will vary slightly based on the FIDO2 token you have chosen. Keep this in mind when evaluating your options.
As an Azure Active Directory user in an Azure AD Tenant where Passwordless Authentication is enabled (see below on enabling an Azure AD Tenant for FIDO2 Passwordless Authentication) navigate to the MyProfile Azure User Portal and select the Security Info menu on the left.
From here we can add methods for sign-in. Security key is the method for registering FIDO2 tokens with your user account. Select Add method => Security key => Add
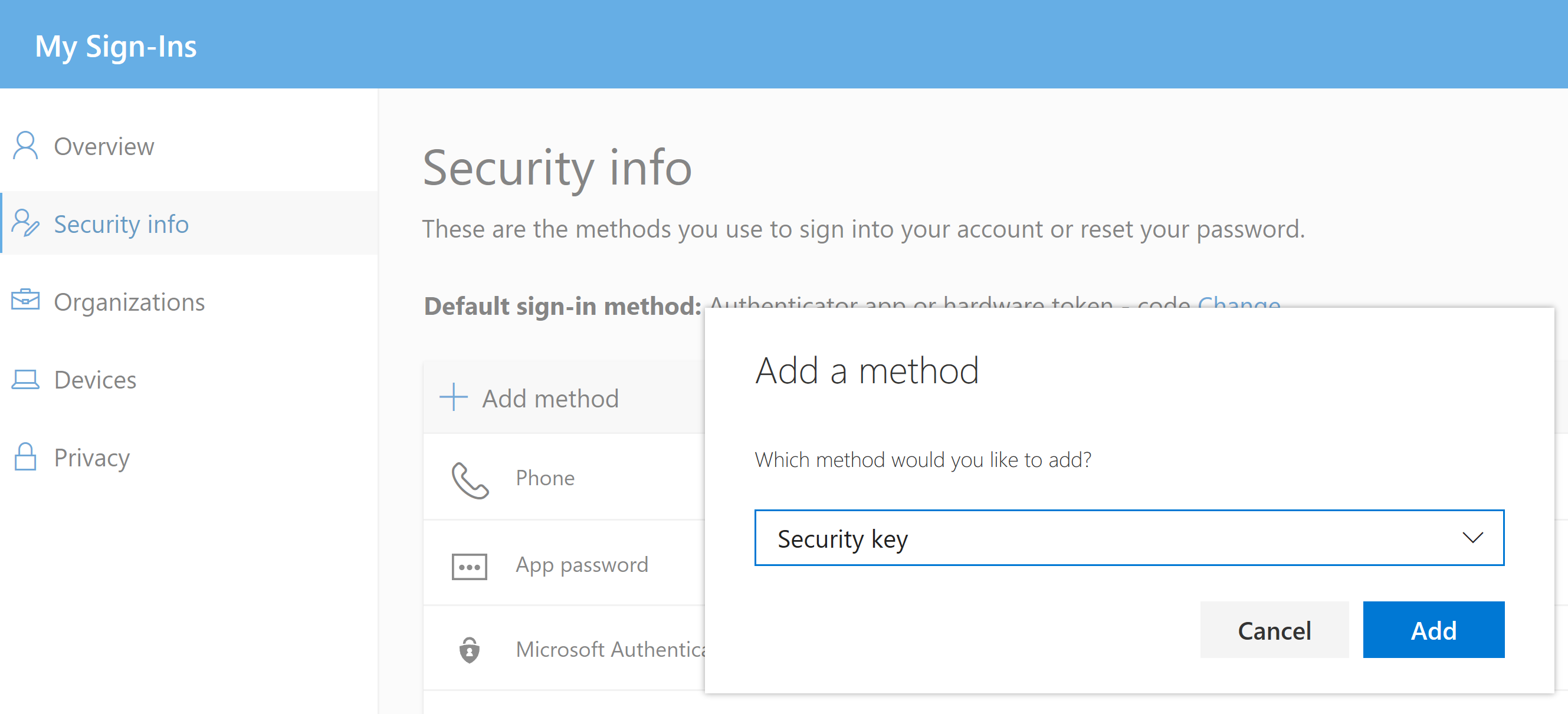
You will be prompted for MFA to validate your credentials again to ascertain that it is actually you that is adding another authentication method to your account. Select Next.
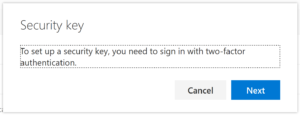
Select the appropriate option for the Security Key you are setting up. NFC or USB FIDO2 Security Token.
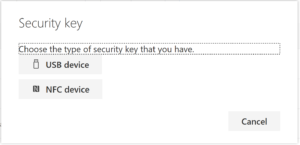
Have your key ready. Select Next
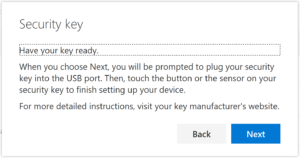
Insert your FIDO2 Security Key
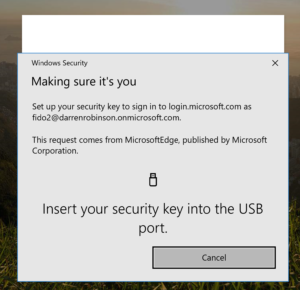
Touch your security key
Provide a name for your security key and select Next
Your FIDO2 Security Key should now be associated with your account. Select Done.
Passwordless Authentication to Windows 10
Now that you have a FIDO2 Security Key associated with your Azure Active Directory user account you can use it to logon to Windows 10. This does assume that your Windows 10 workstation is joined to your Azure Active Directory. If your Windows 10 machine isn’t joined to Azure Active Directory, see “Joining a Windows 10 machine to Azure Active Directory” at the bottom of this post.
This process will differ slightly depending on the type of FIDO2 security key you have. The left column shows the user experience with a bio-metric token. Authenticating to Azure AD requires inserting the token and passing the bio-metric scan. The right column shows a non-bio key whereby a PIN is used to validate the owner of the key and then a tactile touch of the key completes authentication and login to Windows 10 via Azure AD proceeds.
Enable an Azure AD Tenant for FIDO2 Passwordless Authentication
To enable Passwordless Authentication to Azure AD, configure the Authentication methods under Azure Active Directory in the Azure Portal here.
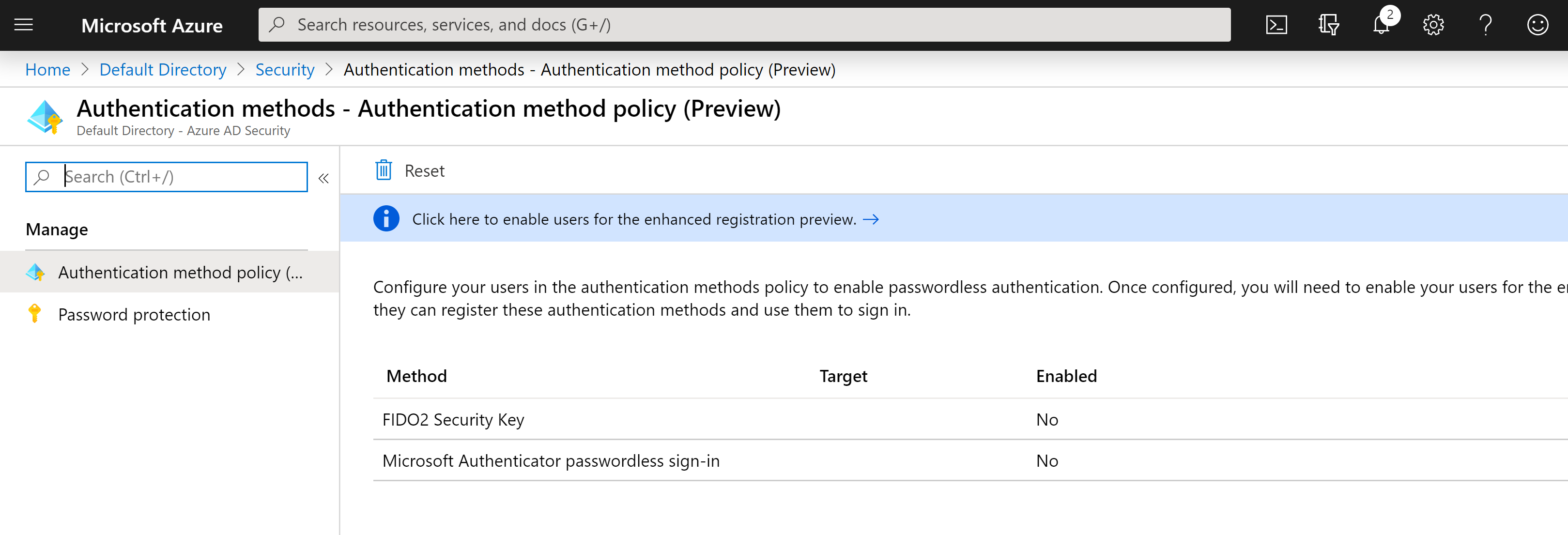
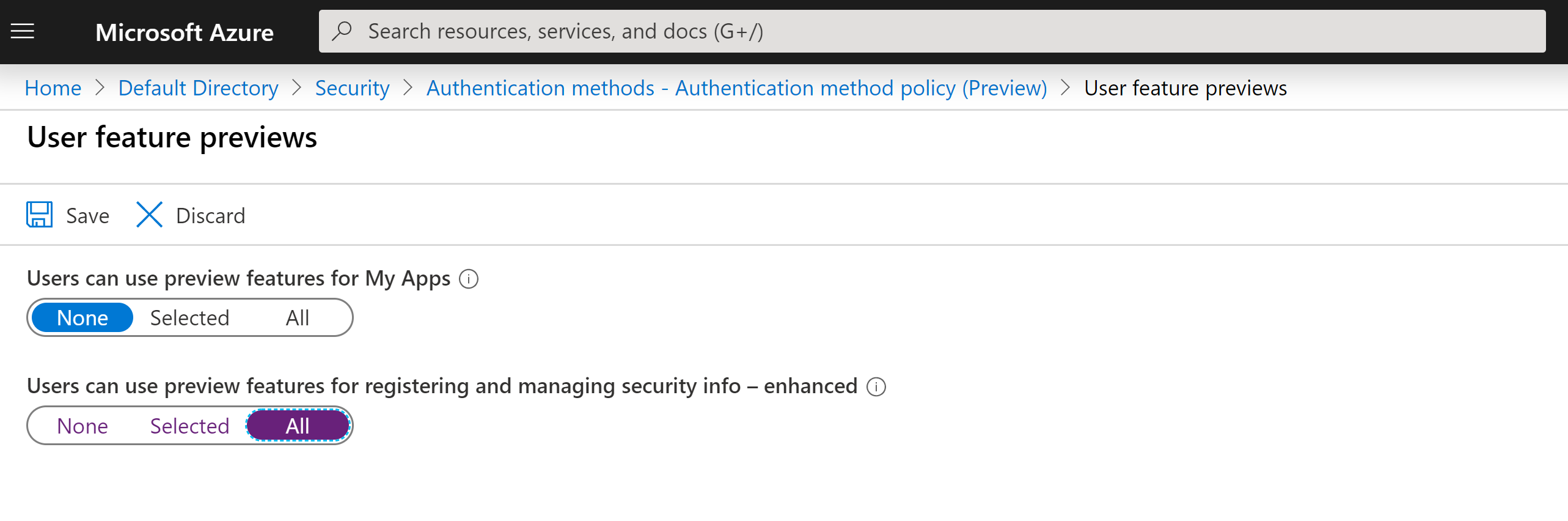
As this is currently a preview feature you will need to enable the enhanced registration process. Select ‘Selected’ or ‘All’ depending on who you will be enabling this feature for and select Save.
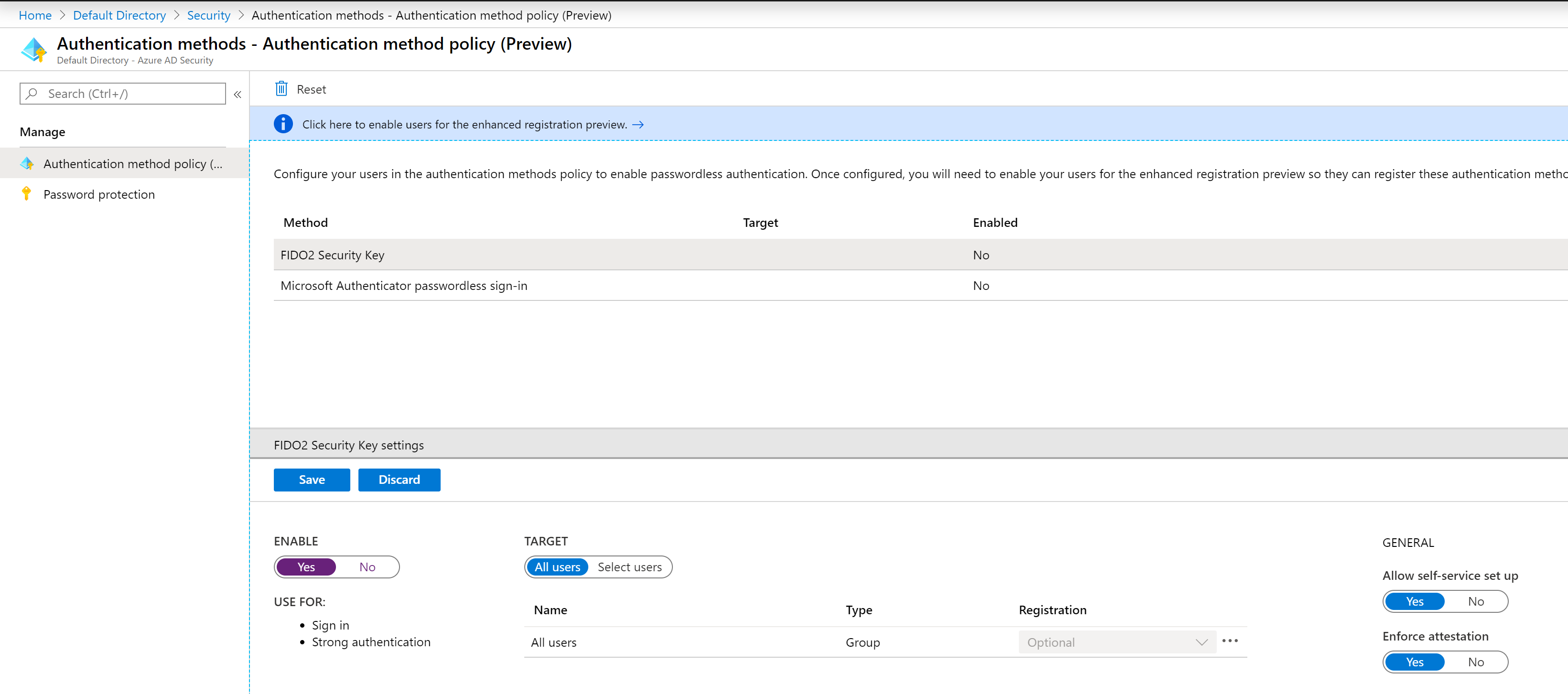
Back in Authentication Methods we can now enable FIDO2 and select Save.
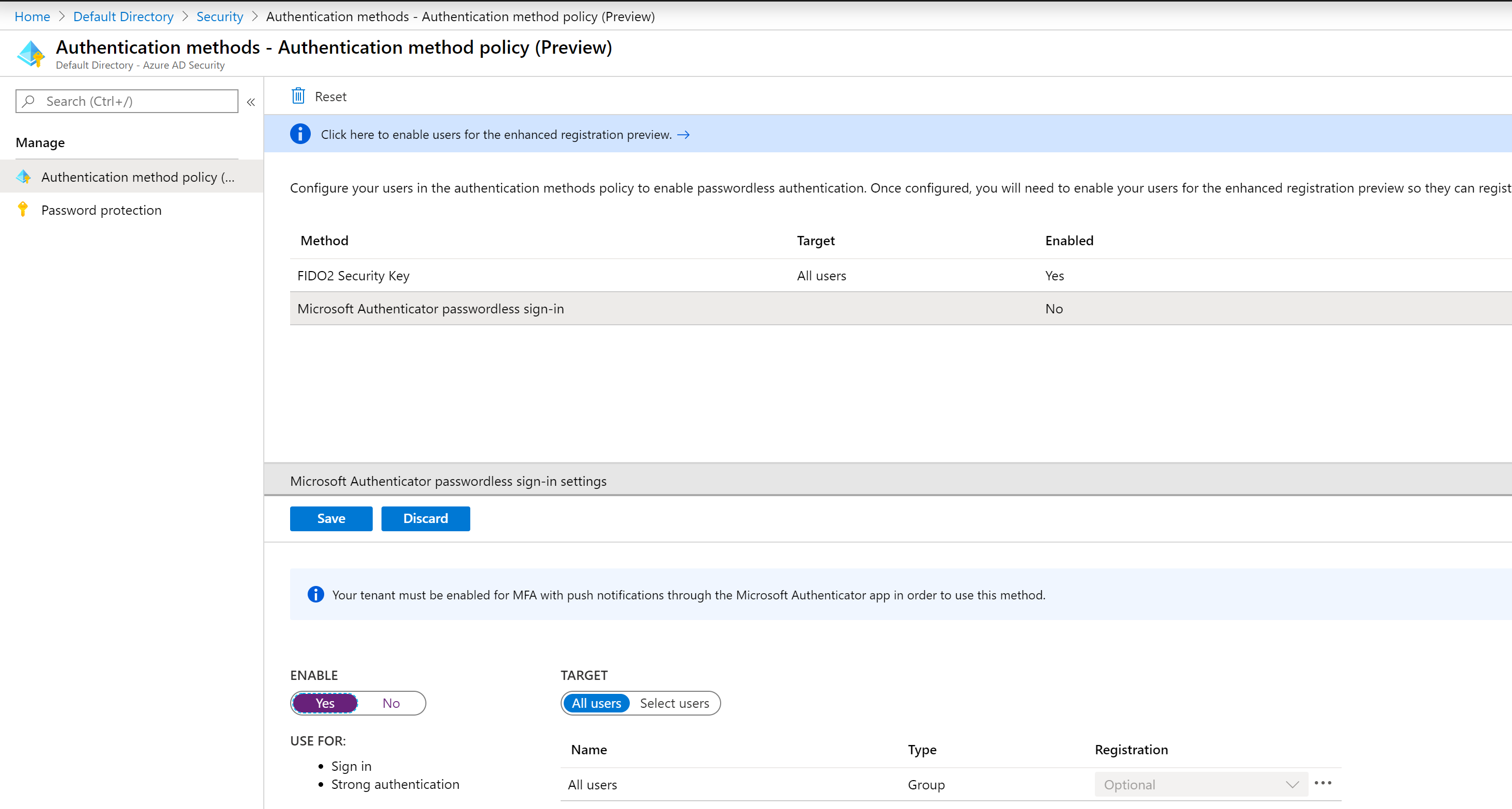
While you are here, you many also want to enable Microsoft Authenticator passwordless sign-in. Note: I won’t be covering mobile base sign-in in this post.
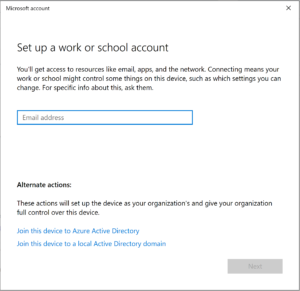
Joining a Windows 10 machine to Azure Active Directory
On a Windows 10 machine navigate to Settings => Accounts => Access work or school => Connect => Join this device to Azure Active Directory, then enter your email address/UPN for the Azure AD Environment and press Next.
On next screen you have to enter your password and then you will be prompted for MFA.
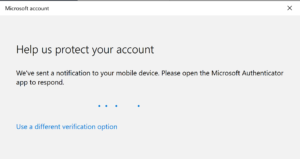
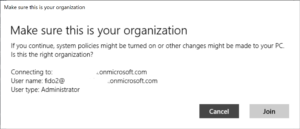
Confirm the join by selecting Join
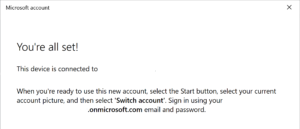
You have then completed joining your Windows 10 machine to Azure AD.
Summary
Choosing a hardware token initially looks trivial. However, when you dig a little deeper you quickly learn there are numerous criteria to carefully consider before selecting a token that will become a key item in your pocket/bag and part of your daily authentication routine. Hopefully I’ve given you enough information to allow you to make an educated decision that is right for you.








