I’m curious. I often think, how does that work? Or why does it behave like that? We are well into the journey towards Passwordless adoption and I’ve spoken and posted about aspects of it before. Always a good place to start are the standards. In this case the FIDO2 standards. But it is also about the implementation of those standards. In a Microsoft Azure Active Directory world, what does your Azure AD FIDO2 Passwordless Credential look like?
So this is something I went down the rabbit hole of a few weeks back wondering what my stored Azure AD FIDO2 passwordless credential actually looked like. I had previously messed around with Authentication Methods as exposed by the Microsoft Graph but this doesn’t really reveal much.
After a lot of digging and some trial and error I was able to return Azure AD FIDO2 Passwordless Credentials from Azure Active Directory. Specifically FIDO2 credentials from hardware tokens. These aren’t currently exposed via Microsoft Graph, but are available using the soon to be deprecated Azure Active Directory Graph. But not just the Azure AD Graph 1.6 version API, but the little known or documented 1.6-internal version API and the User endpoint and the searchableDeviceKey attribute.
With a little manipulation we can get the certificate of an Azure AD FIDO2 Passwordless Credential. The screenshot below is for a registered YubiKey 5Ci.
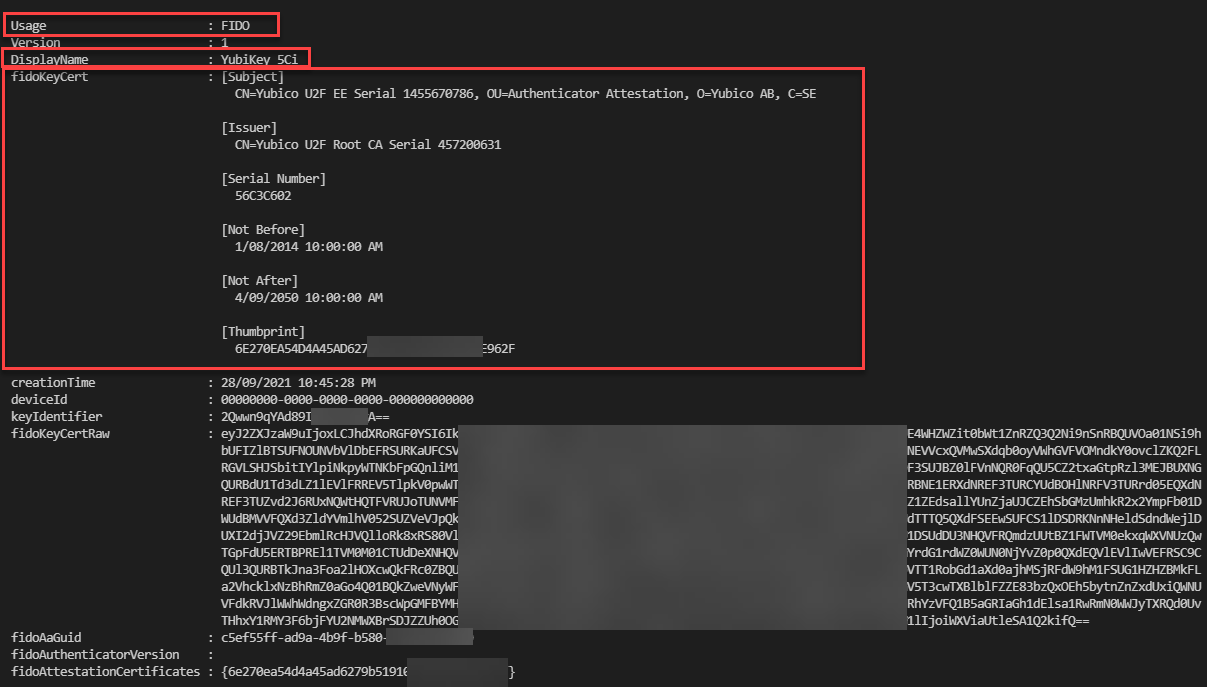
For my inquisitive testing I registered a series of different vendor FIDO2 hardware tokens. Yubico, Feitian and TrustKey (formerly eWBM). The only significant difference between vendors is the issuer of the certificate and in the case of biometric based tokens their features for aspects such as proof of possession (biometric over PIN).

Want to have a look yourself?
If you want to have a look at your Azure AD FIDO2 Passwordless Credential(s) here is the PowerShell script that will let you do that. I’ve tested it with both Windows PowerShell and PowerShell 7.x. It uses the well-known Azure AD PowerShell Client ID and Delegated Permissions (so you will only be able to look at your registered credentials).
It uses the MSAL.PS PowerShell Module to simplify authentication and authorisation to the Azure Active Directory Graph. See this post if you aren’t familiar with it and need to install it.
Make the following changes to use it for yourself.
- Update Line 8 for your Azure AD Tenant name.
- this can be a registered AAD Domain name (e.g., yourcompany.com), the tenantname.onmicrosoft.com or the Tenant ID
- Update Line 9 with your user UPN
Running the script will initiate authentication via your browser to Azure AD. Look for the browser pop up window to authenticate.
Summary
This post showed how to look into Azure Active Directory and peek at FIDO2 Tokens registered for Passwordless Authentication. Of course, there are other methods such as the Microsoft Authenticator Application. That however is maybe details for a future post.


