Azure AD Registered Applications are the Azure AD version of Active Directory Service Accounts. Over time, the number of them grow and grow, each having permissions to consume information from Azure AD and or Microsoft Graph. As an Administrator of Azure AD there is maintenance associated with these Registered Applications, namely credential validity and more important application validity.
Credential expiration associated with Azure AD Registered Applications is quickly visible via the Azure Portal. We can quickly see Current, Expired and Expiring Soon credentials as shown in the screenshot below.
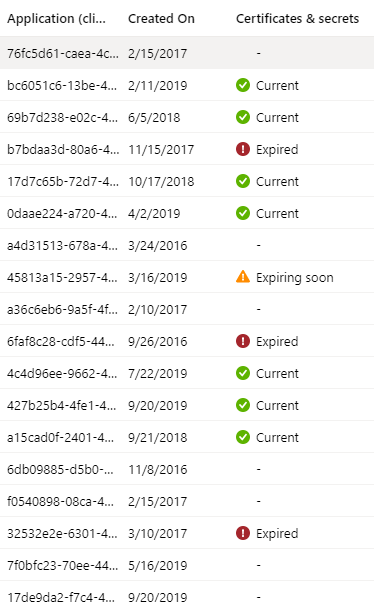
But what about activity associated with the registered apps? For that we need to drill down into each individual application to see sign-in activity.
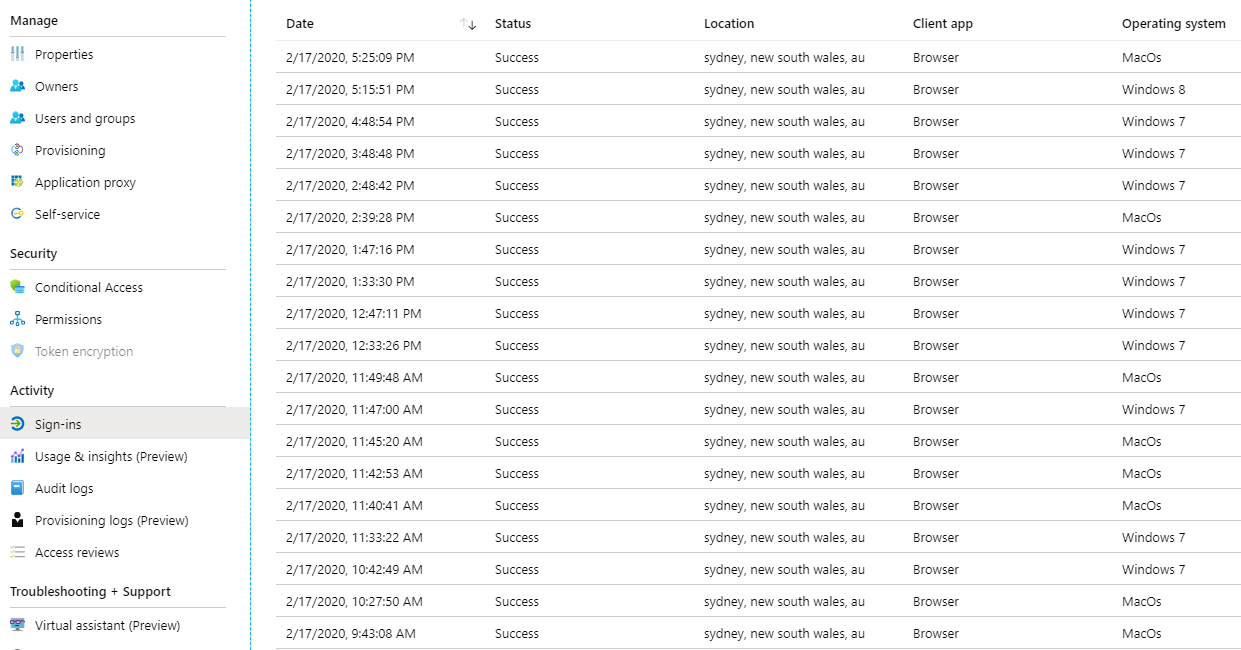
However, what if we have 100’s or 1000’s of Azure AD Registered Applications? How can we programatically inspect each registered application and see if the credentials have or are about to expire, along with if the application is actively being used? That is what this post covers.
Prerequisites
It is rather ironic that in order to query Microsoft Graph to Audit Azure AD Registered Applications and Sign-In Activity we will need a Registered Application with the necessary permissions. Register a new app if you don’t have one with the following permissions, or use/update an existing app that has;
- Registered Applications enumeration
- in order to enumerate all the Registered Apps you will need a Registered Application with;
- Microsoft Graph => Directory.Read.All
- in order to enumerate all the Registered Apps you will need a Registered Application with;
- Azure AD Audit Logs
- in order to search for sign-in activity associated with Registered Apps
- Microsoft Graph => AuditLog.Read.All
- in order to search for sign-in activity associated with Registered Apps
The script below uses the MSAL.PS PowerShell Module. You will need this installed on the host running the script.
- The MSAL.PS module is used for Microsoft Graph Authentication. See this post for more details.
Example Script
Here is an example script that authenticates to Microsoft Graph leveraging a registered application you have registered with the permissions listed above.
Update:
- Line 2 for your AAD Tenant ID
- Line 3 for your AAD Application ID
- Line 4 for your AAD Application Secret
- Line 10 for the number of days in advance you are looking to check for expiring credentials (e.g credentials expiring in the next 60 days)
After running the script you will have two collections.
- $expiringCredsApps collection contains Registered Applications that contain a credential that is expired or will be expiring in the next 60 days (as per the configuration value on line 10.
- The collection objects also contain recent Sign-Ins
- $aadAppsReport collection that contains all Registered Applications along with recent Sign-Ins and credentials
Summary
Using PowerShell and Microsoft Graph we can quickly enumerate and Audit Azure AD Registered Applications. You can easily expand on this script and schedule its execution and enable a notification.

