Microsoft have just announced the Public Preview for Hardware OATH Tokens such as the Yubico YubiKey with Azure MFA. In this very long and graphic heavy post I show the end-to-end setup and use of a YubiKey physical token from Yubico as a Multi-Factor Authentication (MFA) second factor authentication method to Azure AD/Office 365.
Specifically I detail;
- the user experience using a YubiKey Hardware Token with Azure MFA
- the administrator configuration process for admin enabled YubiKey physical tokens for use with Azure MFA
- a user enrolling a YubiKey physical token as an additional method for use with Azure MFA
- switching second-factor authentication methods when authenticating to Azure AD / Office 365
For the process I show here;
- the Admin account I’m using to do the configuration is a Global Admin
- the user I’m enabling the token for
- is assigned an Enterprise Mobility + Security E3 license
- is enabled for MFA
- was enrolled in MFA using the Microsoft Authenticator App.
Authenticating to Azure AD/Office 365 with a YubiKey for MFA
Before I get into the configuration and setup, here is the resulting process when complete. When authenticating to Azure AD/Office 365 I’m prompted for my Username and Password.
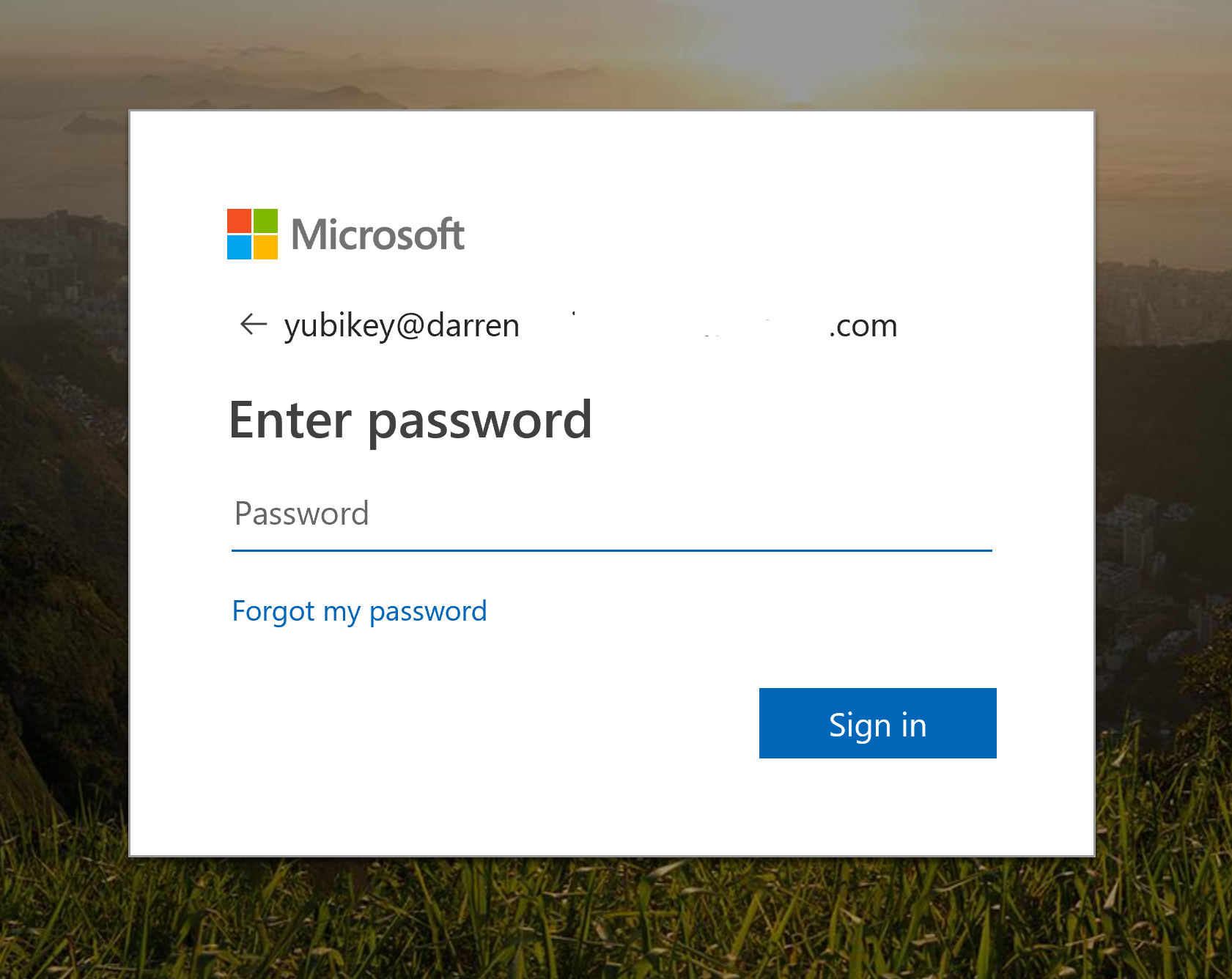
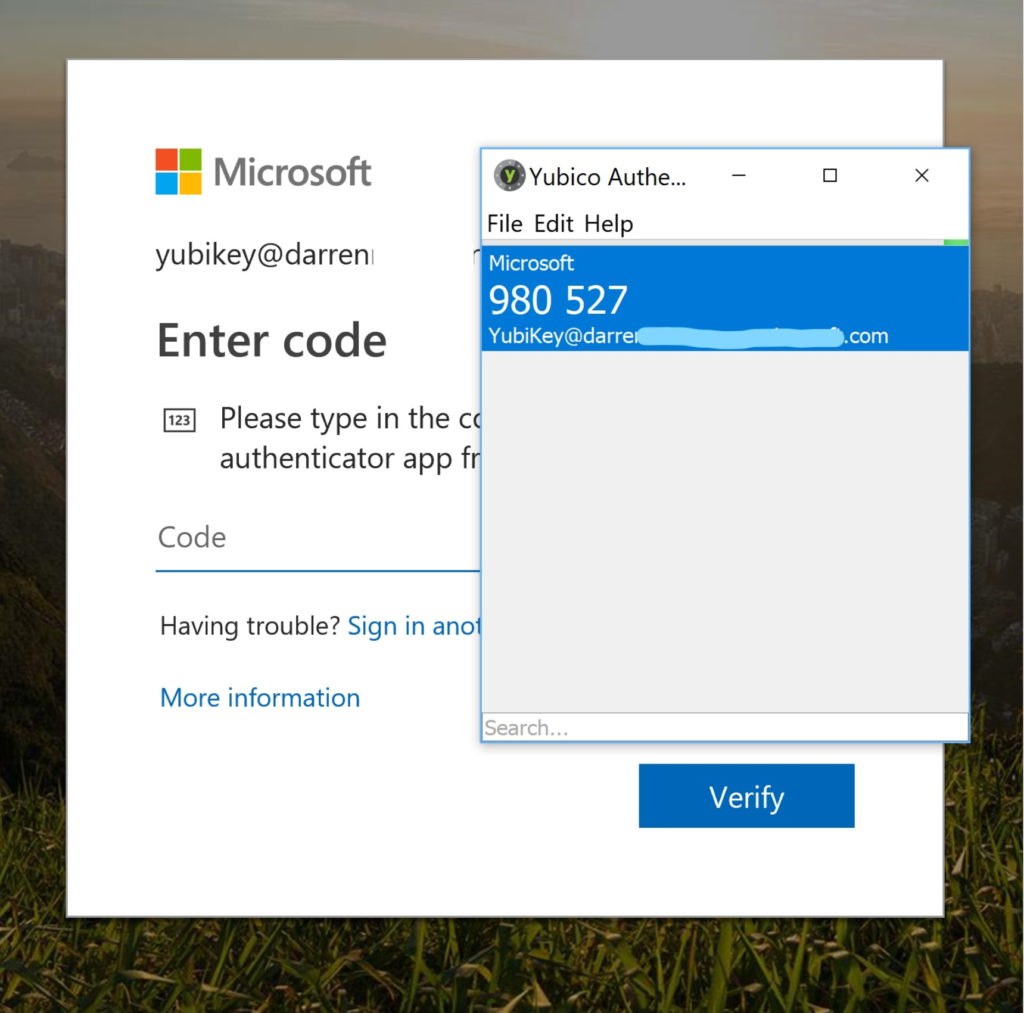
Then I’m prompted for my YubiKey One Time Password (OTP). With the key inserted in my computer ……
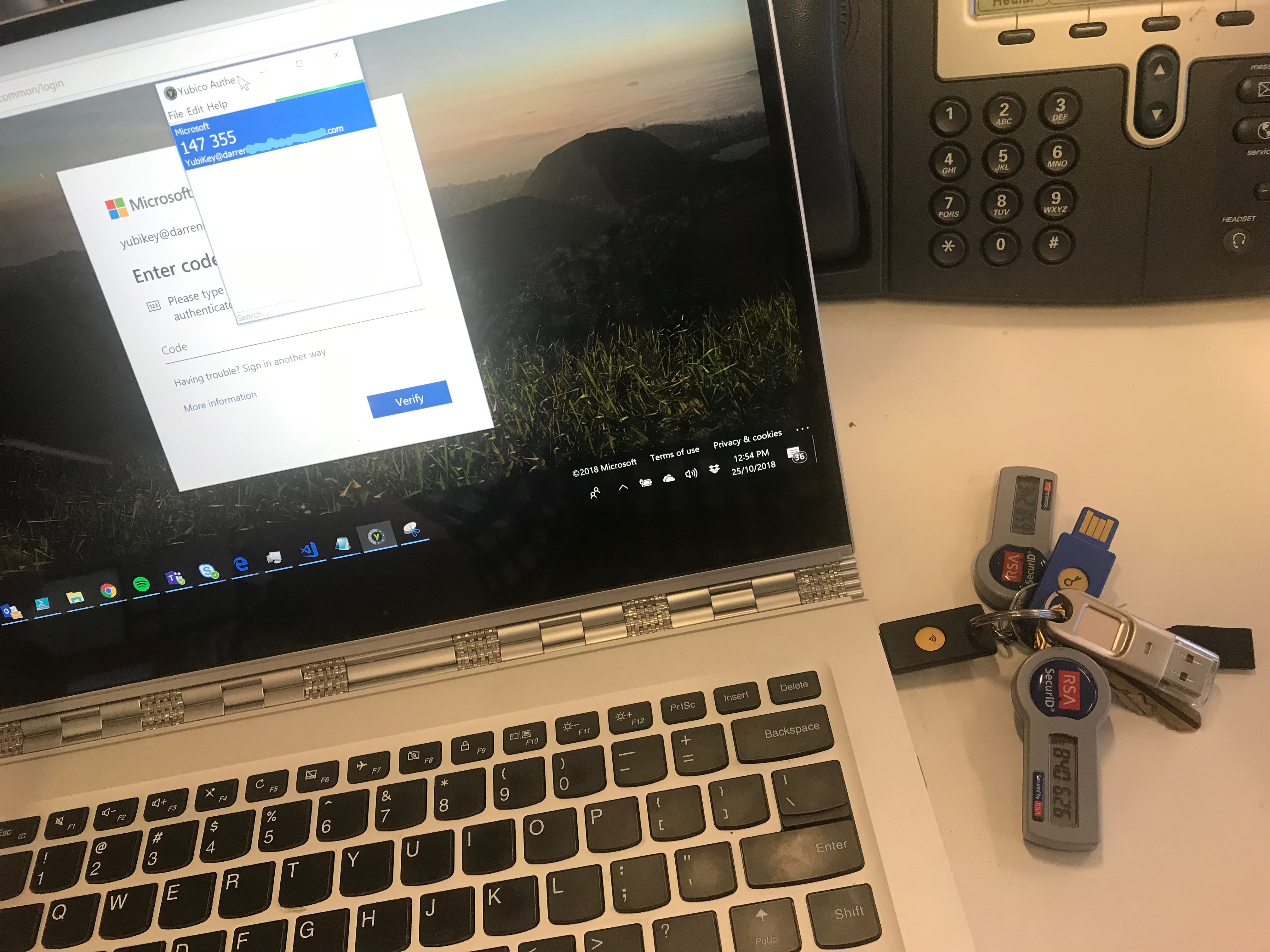
… and the Yubico Authenticator open, the Yubico Authenticator displays the OTP that I can copy and paste the password into the Login Code Window.
Note: The Yubico Authenticator will only display the OTP code for the appropriately configured YubiKey which it is inserted into the same computer running the Yubico Authenticator.
Admin Enabled OATH TOTP Token Assignment
In order to enable physical tokens for use with Azure MFA an Azure Administrator must configure token assignments for users in the Azure Portal. Like other functionality we’ve seen during Public Preview (such as Azure B2B) the method to configure these assignments is uploading a CSV with the necessary information. Hopefully we don’t have to wait too long for a Microsoft Graph/PowerShell Module to complete this step.
CSV Format
The CSV Format is shown below in raw and from VSCode. Essentially token assignment assigns a token to a UPN. The upload will fail if you don’t specify a valid UPN for your tenant.
Note: The header row must be present and don’t use quotes.
upn,serial number,secret key,timeinterval,manufacturer,model YubiKey@darren.customer.com.au,9876543,PFXXKIDENFSG4J3UEB2GQ2LONMQGSJ3EEB2XGZJAMEQHEZLBNRWHSIDTMVRXEZLUEBSGSZBAPFXXKPY=,30,YubiKey,HardwareKey
![]()
The file is uploaded via the Azure Active Directory => MFA Server => OATH Tokens configuration option. Once you’ve selected Upload and provided the file, the File upload is in-progress dialog is displayed. Select Refresh.
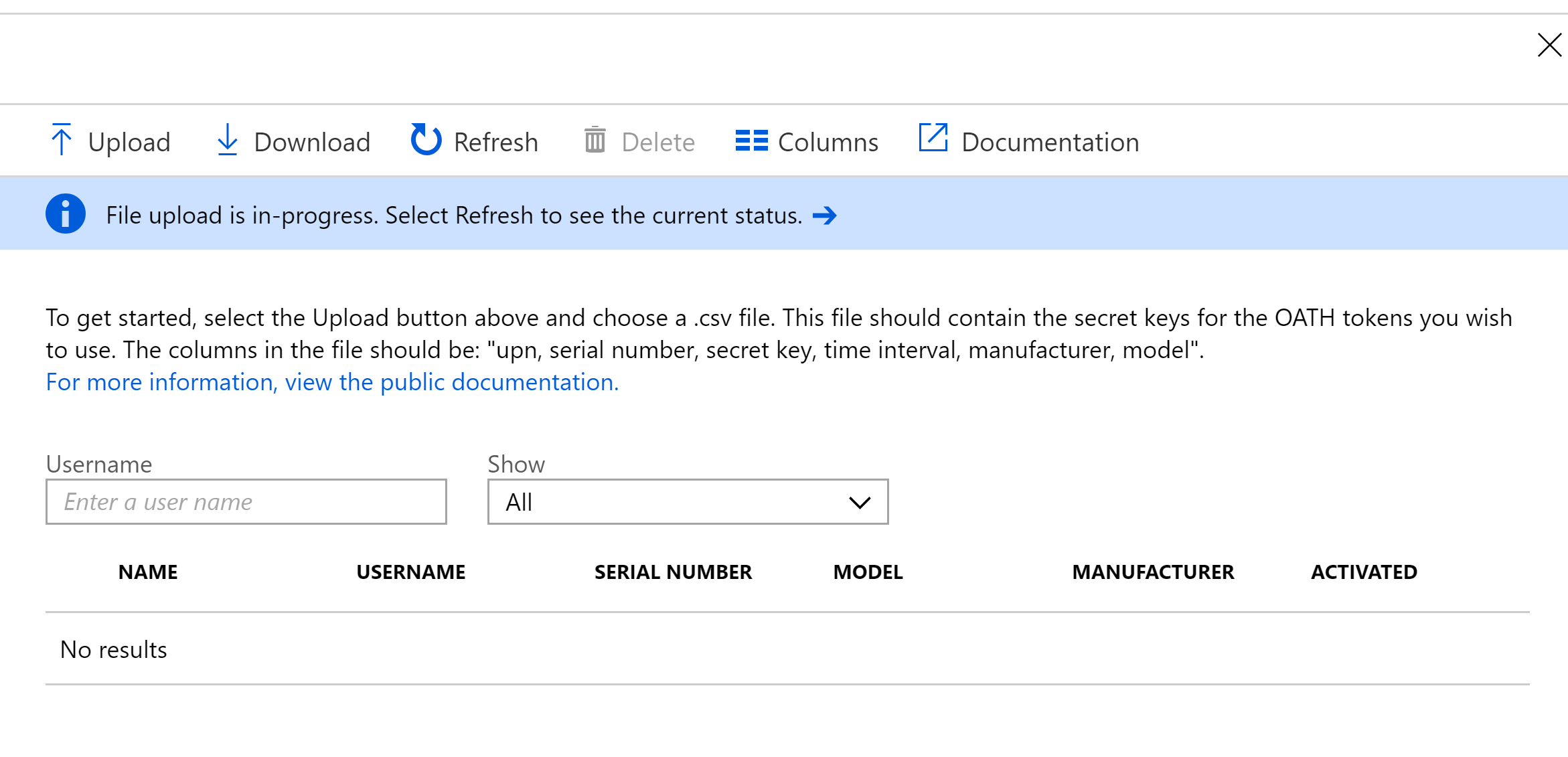
After successfully uploading the CSV and hitting the Refresh button we have the token assignment for the user.
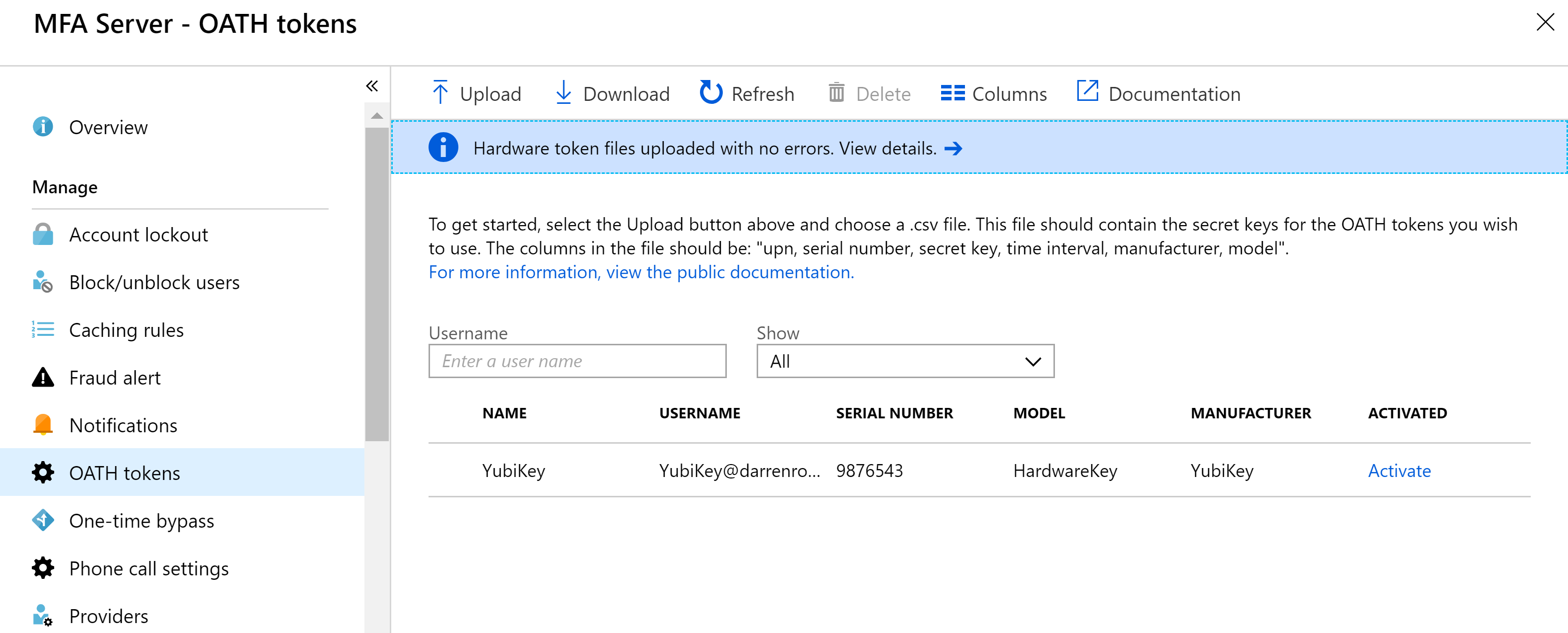
In order to Activate the token you will need to have the Yubico Authenticator Application installed and the YubiKey token configured. That process is shown in the next section below. Once that is complete select Activate from the screen above and enter the OTP code displayed in the Yubico Authenticator for the token enrolled with the associated user.
Enrolling a YubiKey Physical Token with Azure MFA
With a hardware token associated with a user in Azure MFA the user can now enroll with that option. Head to Additional security verification options under the user’s profile and choose Setup Authenticator app
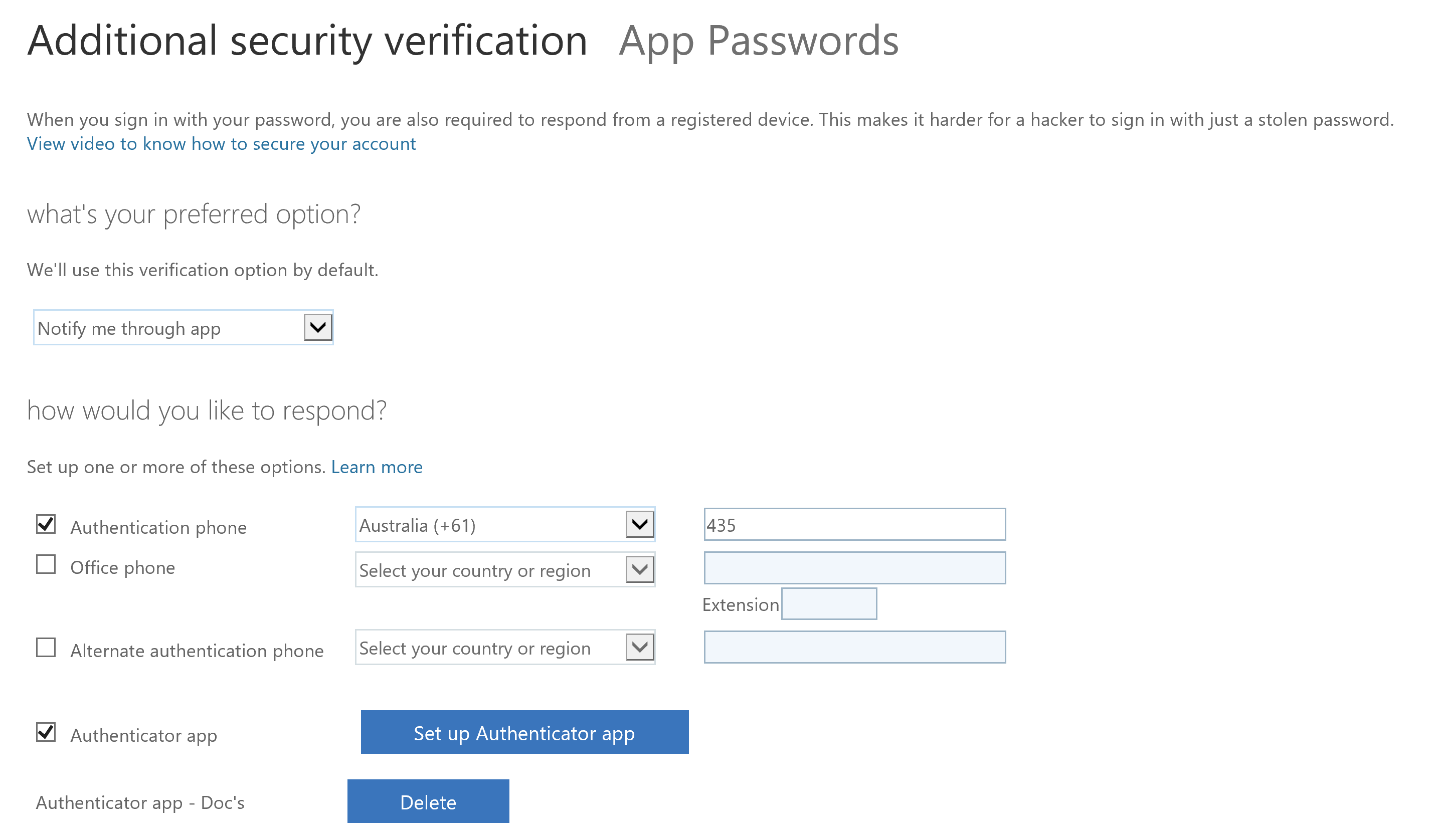
The following option will be displayed. Select the link for Configure app without notifications 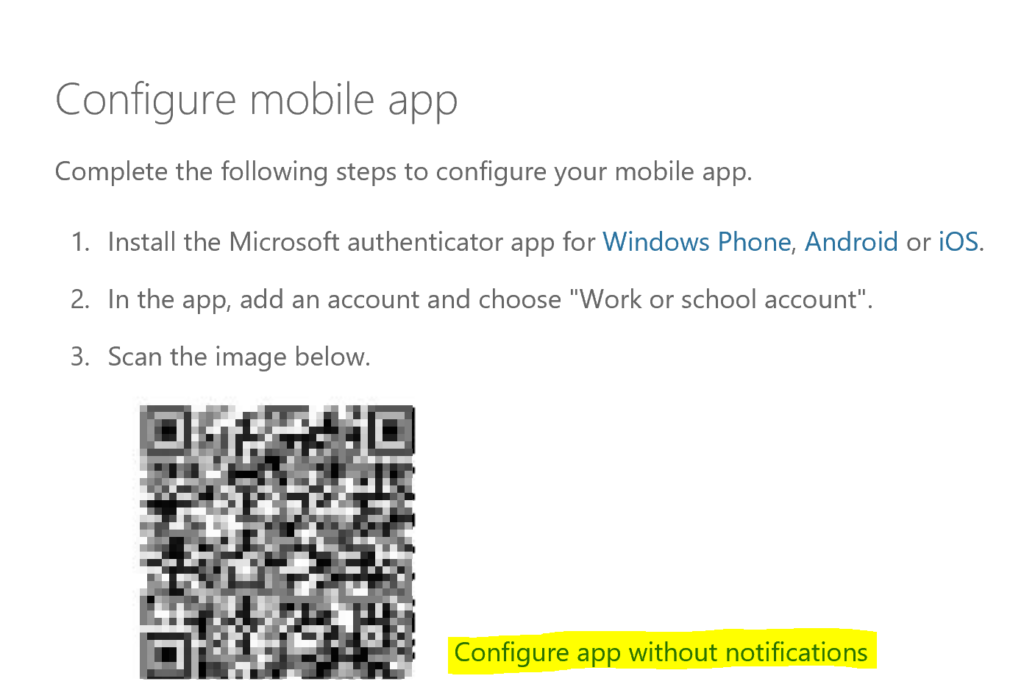
A slightly modified QR Code will be presented. 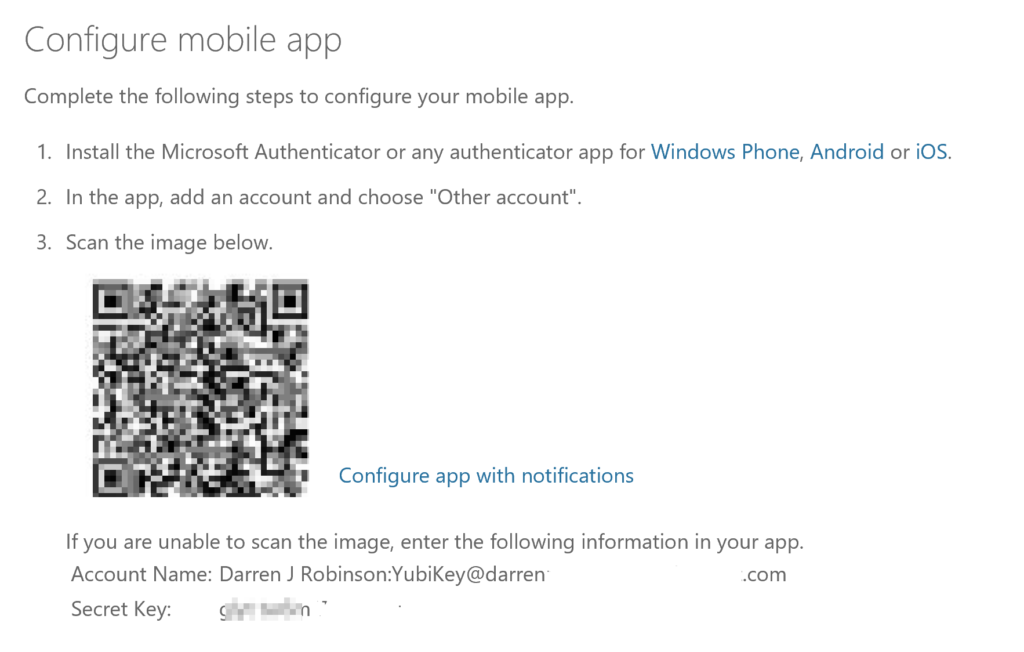
Open the Yubico Authenticator Application and with the YubiKey inserted in the workstation from the File menu select Scan QR Code. The Yubico Authenticator App will magically scan the QR code and configure the credential in the Authenticator App. Select Save Credential. 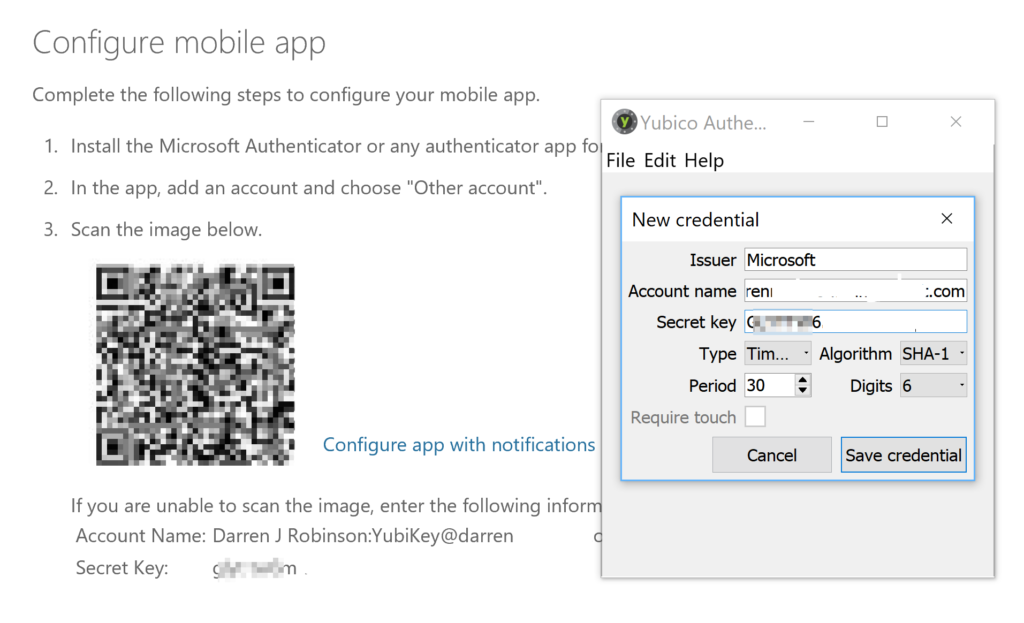
Verification is required. Select Verify now. 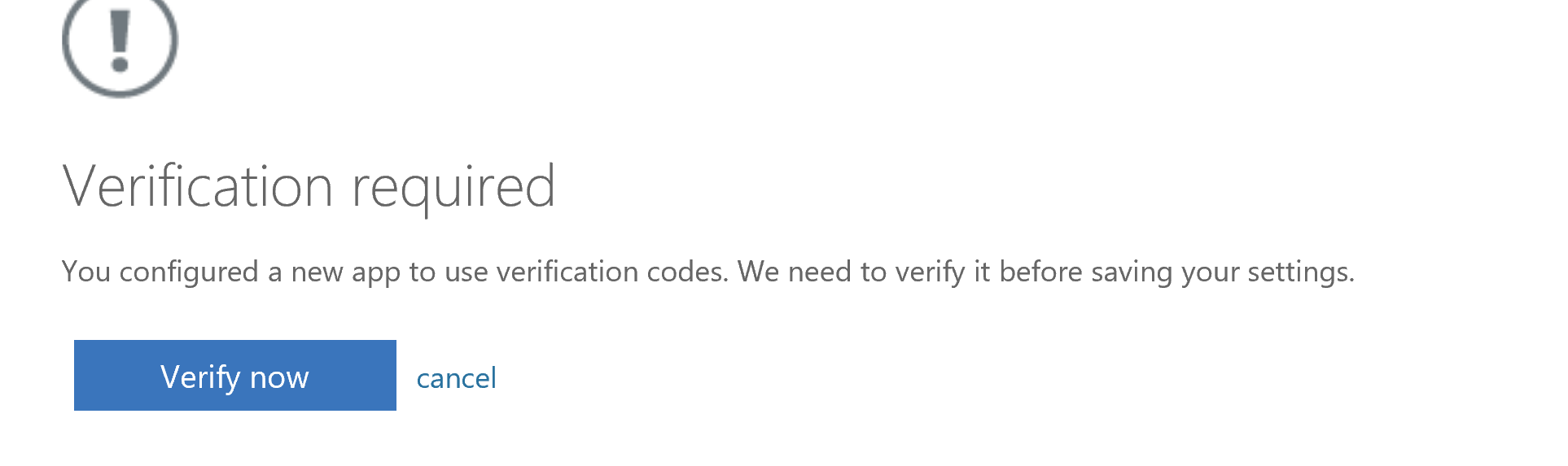
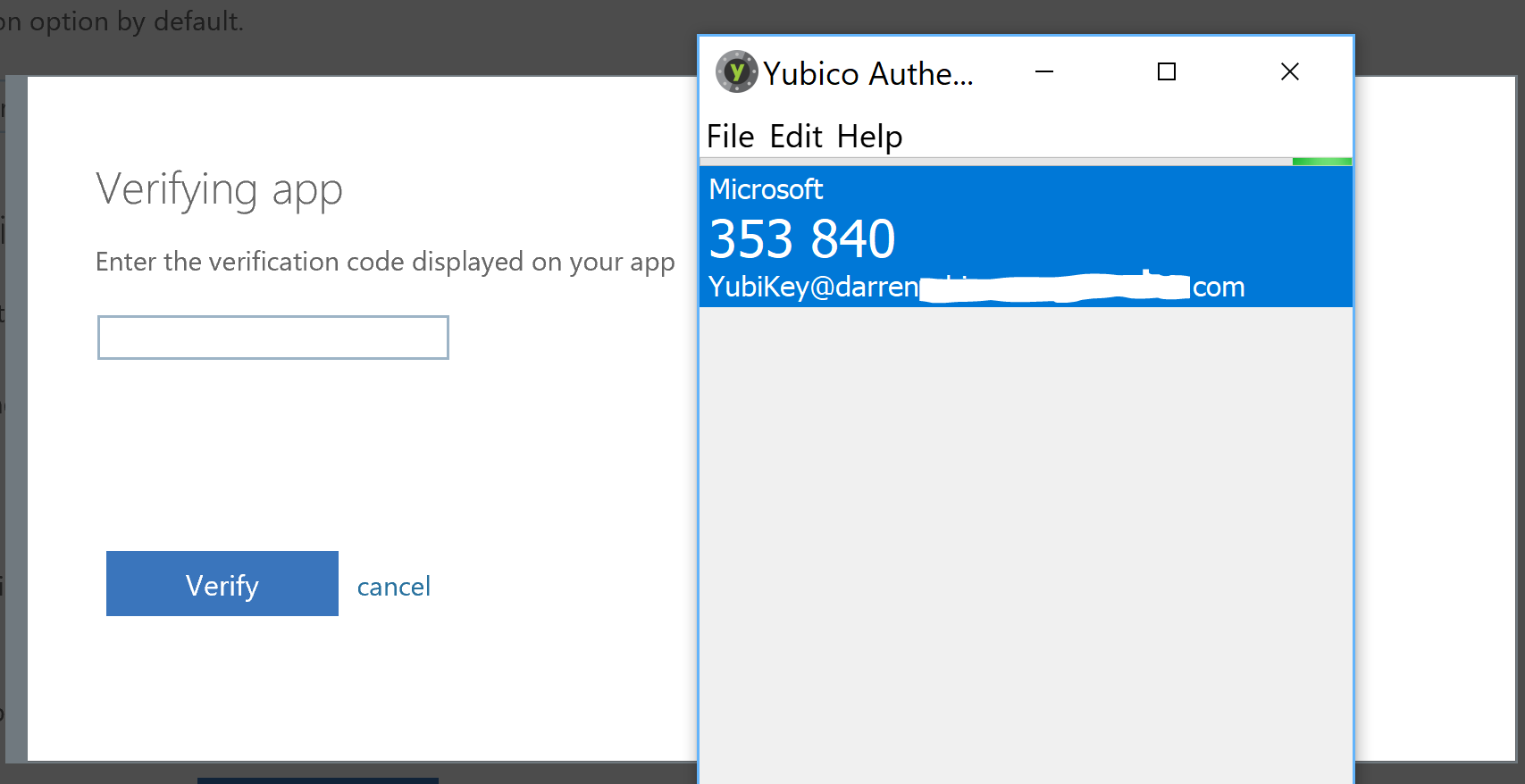
Copy and paste the OTP into the text box and select Verify. 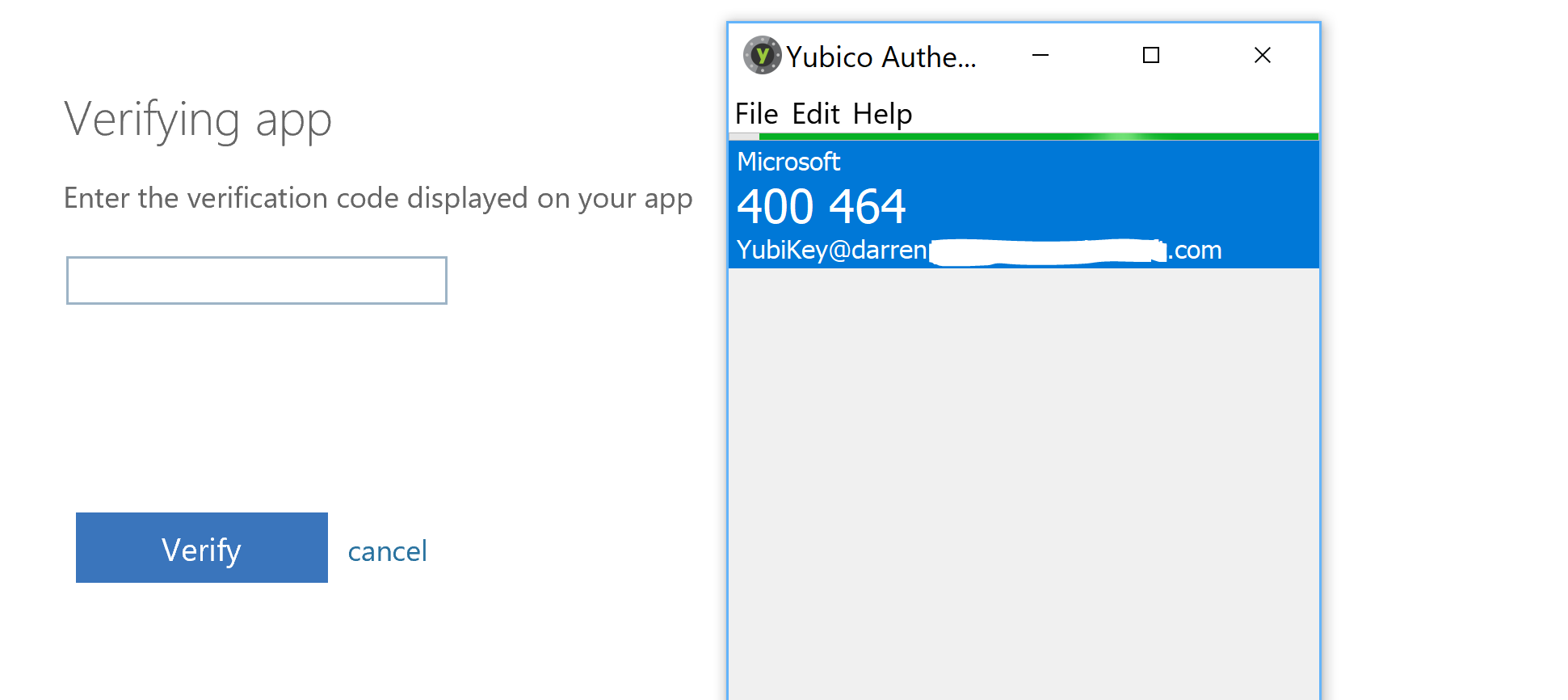
We now have the 3rd MFA method enrolled (Phone, Microsoft Authenticator and YubiKey with Yubico Authenticator). Select Save.
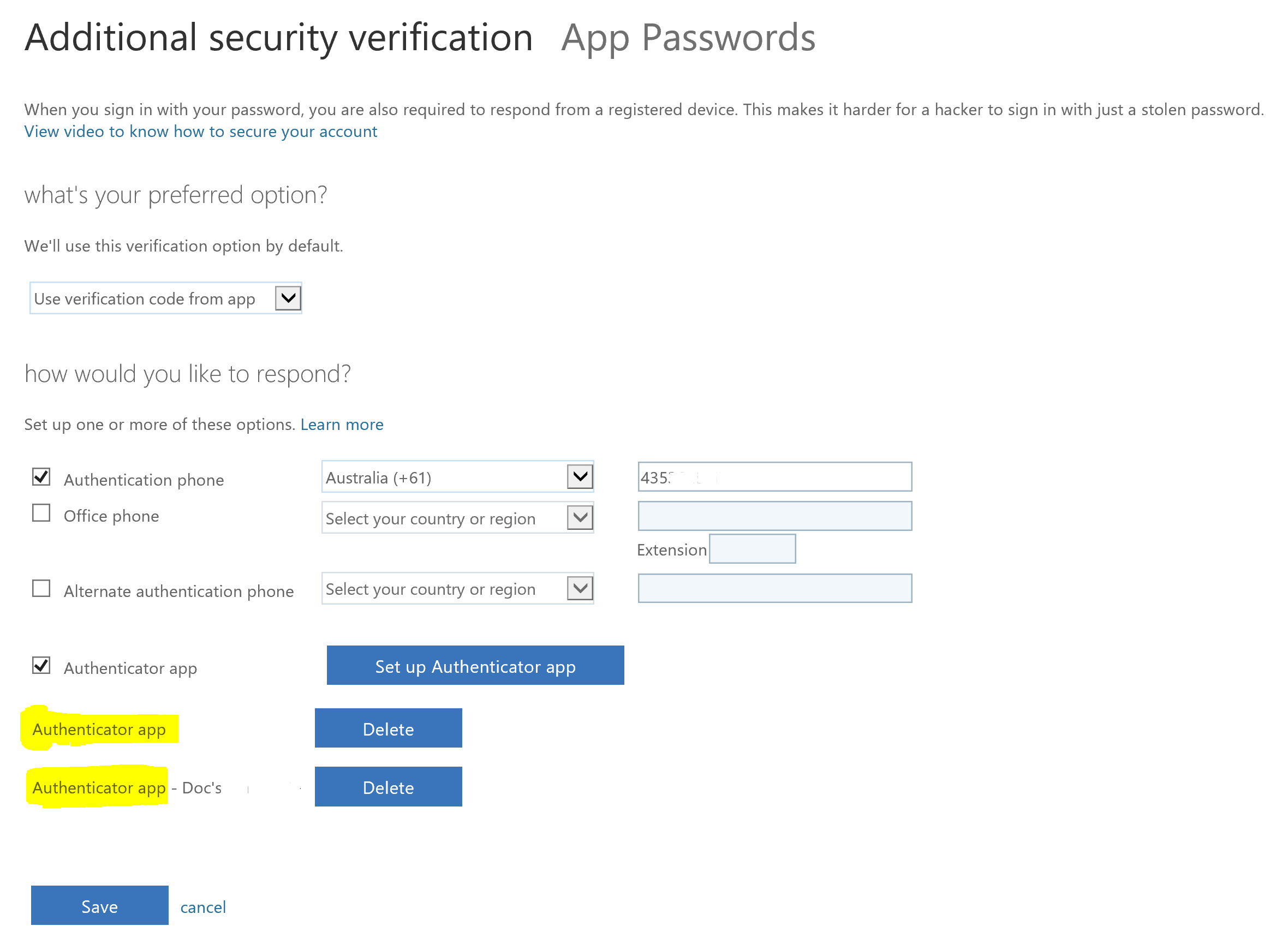
As I now have multiple methods registered and my latest method I just registered is now the default I have to re-verify the new method. Select Verify preferred option.
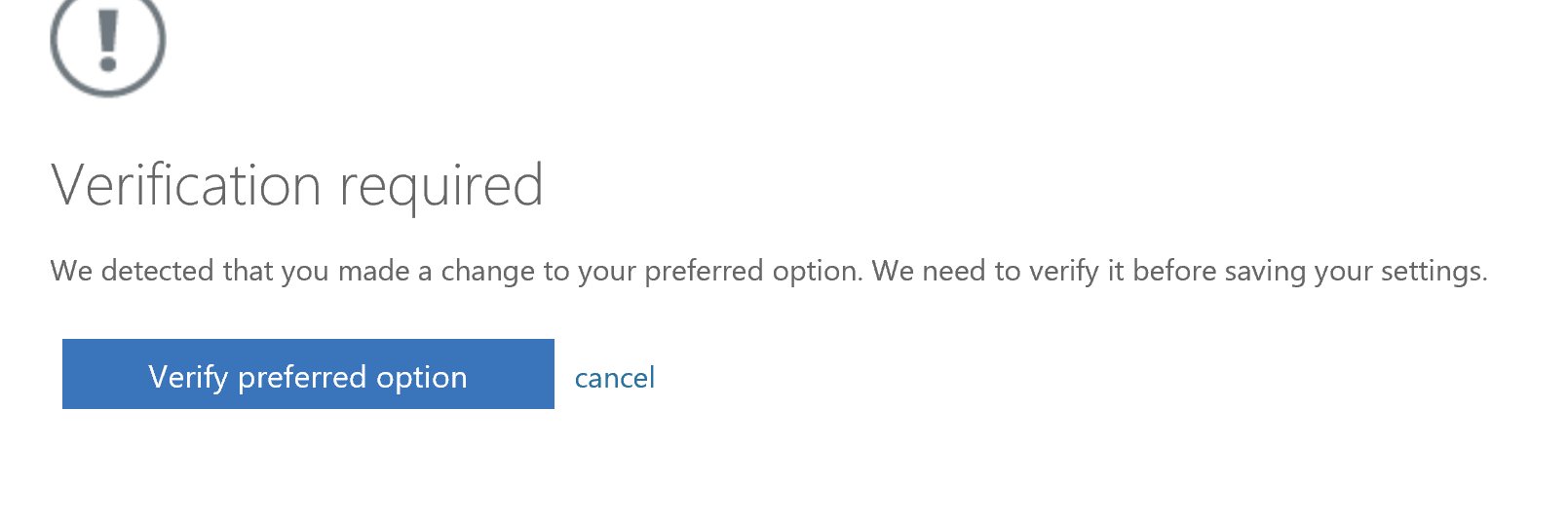
Copy and paste the OTP code into the text box and select Verify.
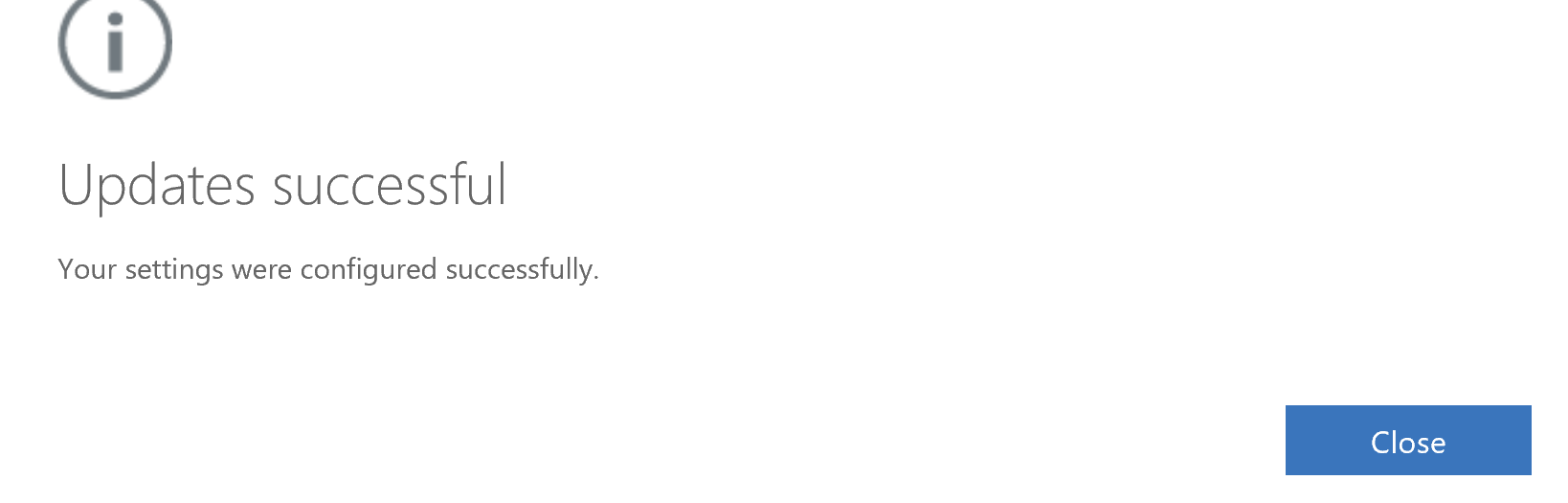
Verified. Update is successful. Select Close.
Back in the MFA Server OATH tokens Admin console for the associated user, select Activate and enter the current OTP code displayed in the Yubico Authenticator.

The token can now be used for MFA as shown at the beginning of this post.
Multiple MFA Methods – Switching MFA Methods
As I already had the Microsoft Authenticator Application registered as an MFA method before I enrolled the physical token I now have multiple methods enrolled. The primary is the token which is fine when using a laptop but as an iPhone user, NFC isn’t an option with YubiKey v5 yet as NFC Write is not enabled on iOS.
On logon after providing my username and password I’m prompted for MFA and I can select Sign in another way
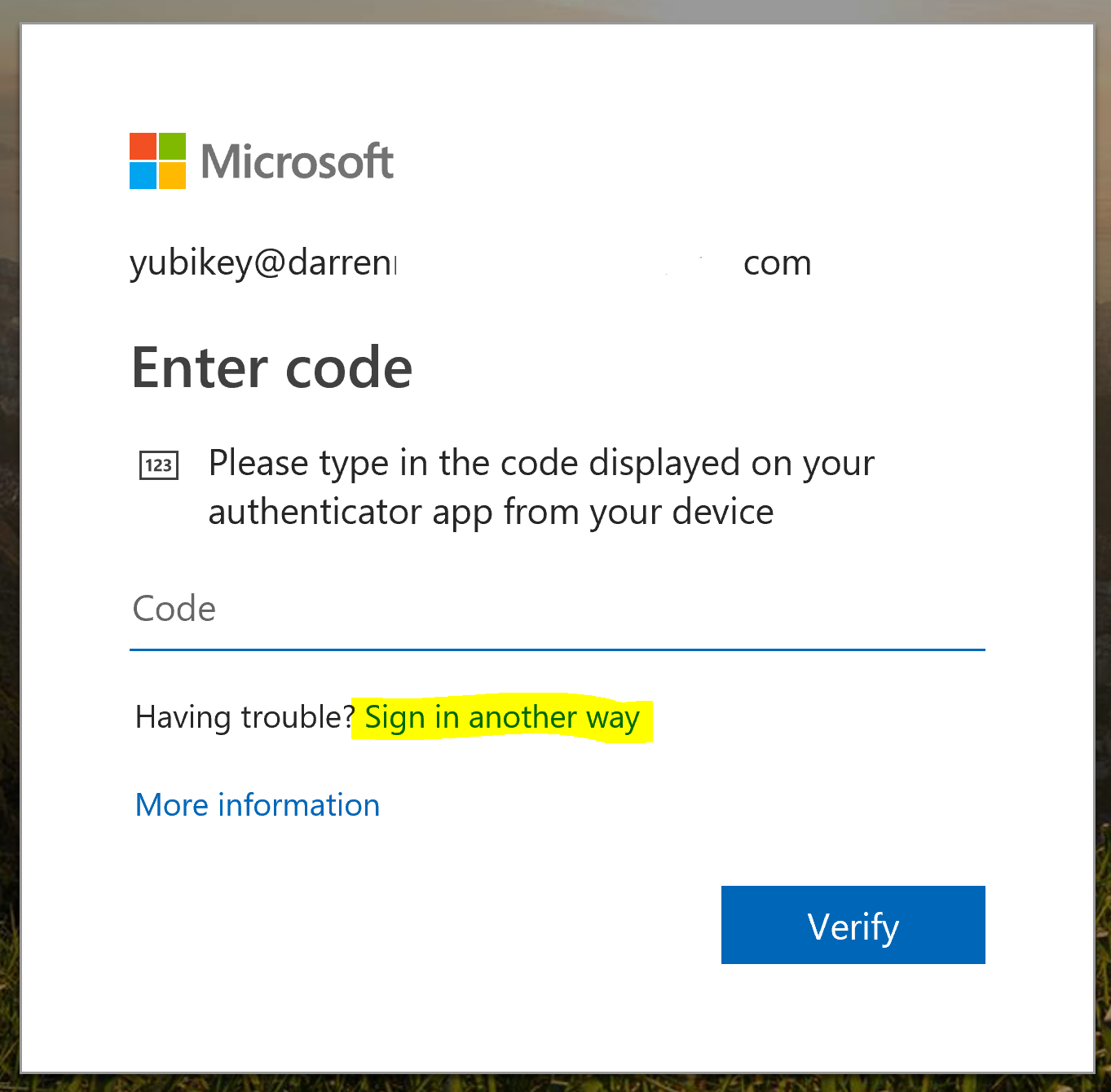
This then provides me with my other enrolled methods and top of the list is the option for Microsoft Authenticator
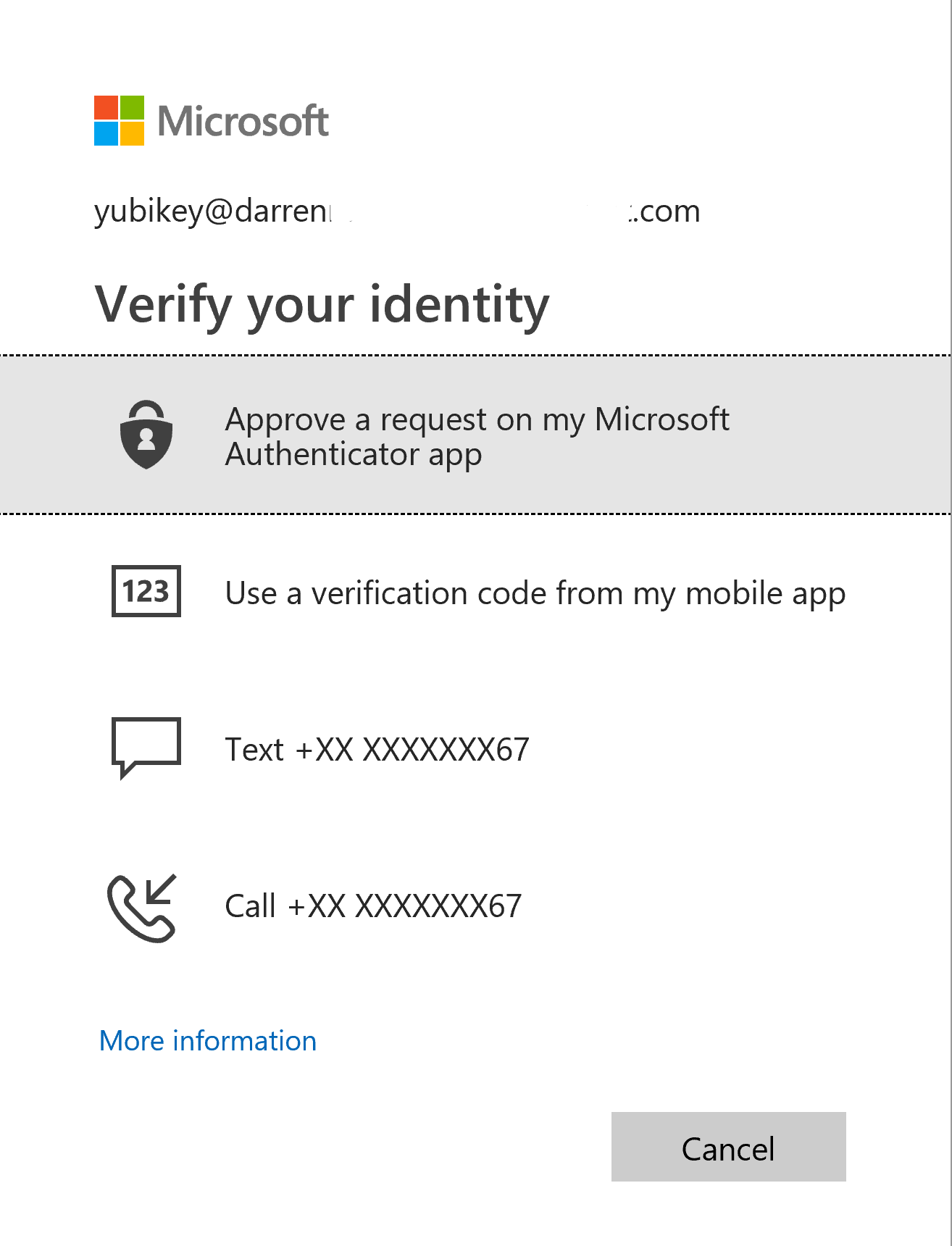
Selecting the Microsoft Authenticator App option I am prompted on my Microsoft Authenticator App for MFA rather than using the primary method of the YubiKey with the Yubico Authenticator. I select Approve and I’m authenticated.
Changing Primary Method
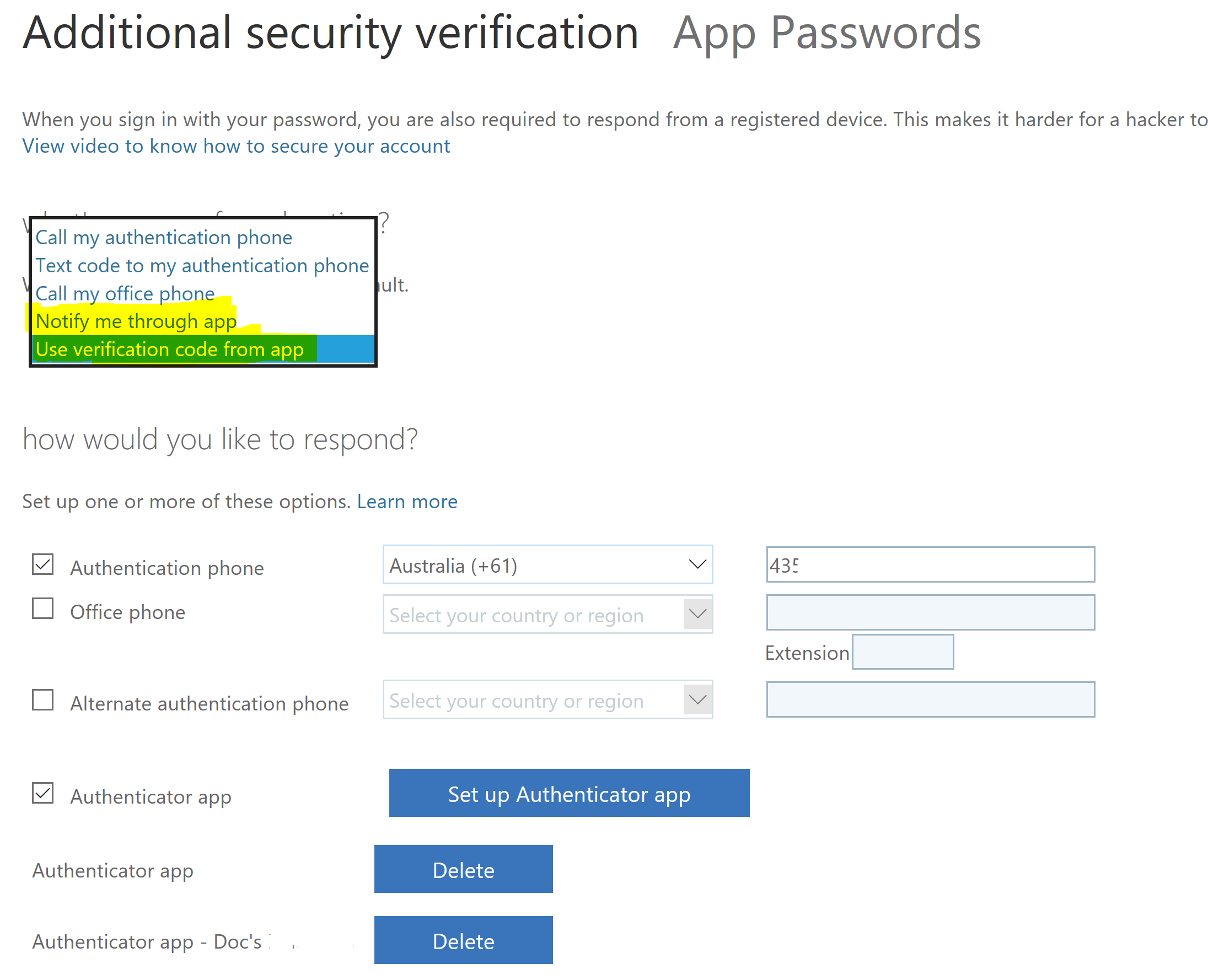
With multiple methods enrolled at some point you may need to change your primary method. Back in the Additional security verification options for the user the default method can be updated. The key bottom two options are;
- Notify me through app
- for me this is the Microsoft Authenticator App
- Use verification code from app
- this is the Yubico Authenticator with the YubiKey enrolled
Summary
Microsoft Azure MFA now supports OATH TOTP Hardware Tokens. Compatible tokens can be registered by an Azure Administrator and assigned to users.
Hardware Tokens can be enrolled to a users profile in addition to other methods (phone call, SMS, Microsoft Authenticator).
Now what would be nice would be via Conditional Access the ability to specify the MFA Factor. e.g. If accessing Application X the only accepted MFA Method is physical token.