Introduction
As the title suggests this is Part 2 of a three-part post on configuring FIM/MIM to synchronise users passwords from AD to the Domino ID Vault via PCNS and FIM/MIM.
Part 1 here detailed the creation of a PowerShell Management Agent to join users from Domino to the MIM Sync Metaverse.
This post details the creation and configuration of the Domino Agents to receive password changes via the PS MA into the ID Vault.
Part 3 here details calling the Domino Agents on password sync events (from PCNS via MIM)
Creating a New Domino Application
As mentioned above and in Part 1 we need to create Domino Agents to process password change events into the ID Vault. Domino Agents are required as Domino security will not allow password change events (called using the resetUserPassword method) to be run remotely. The resetUserPassword method is only supported using the RunOnServer method.
In order to create a Domino Agent we need to install and run the IBM Domino Designer.
With that installed we can start with our first Domino Agent. We will create two Agents. The first will be the one that will perform the execution of the resetUserPassword method. The second will be the trigger that will retrieve the details of the user to change the password for and pass it to the first agent to execute.
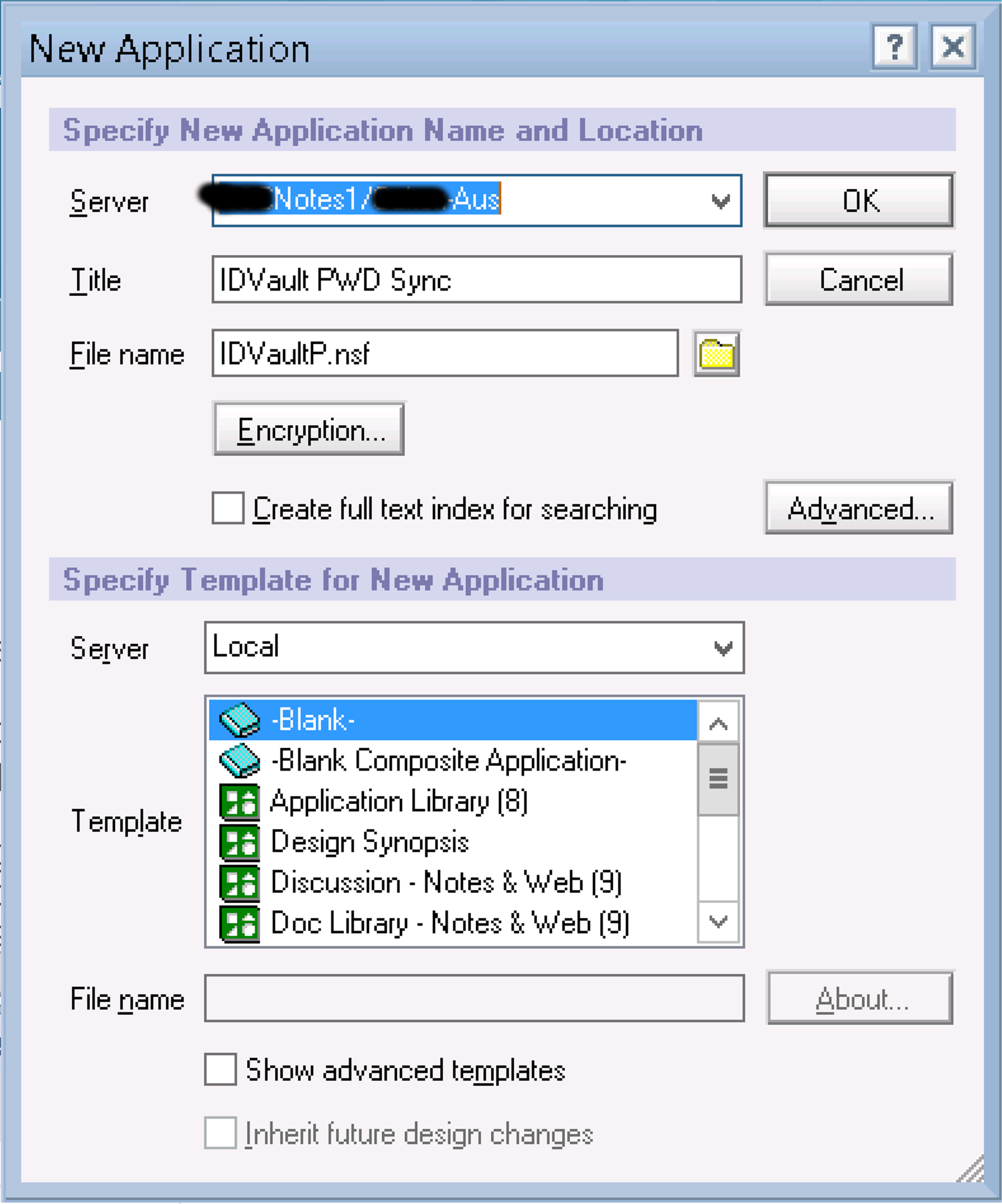
In IBM Domino Designer select File => New => Application
Specify the Server to create the new Application on (and subsequently where it will run) and give the Application a name. I used ID Vault PWD Sync.
Create the MIM Password Sync Domino Agent
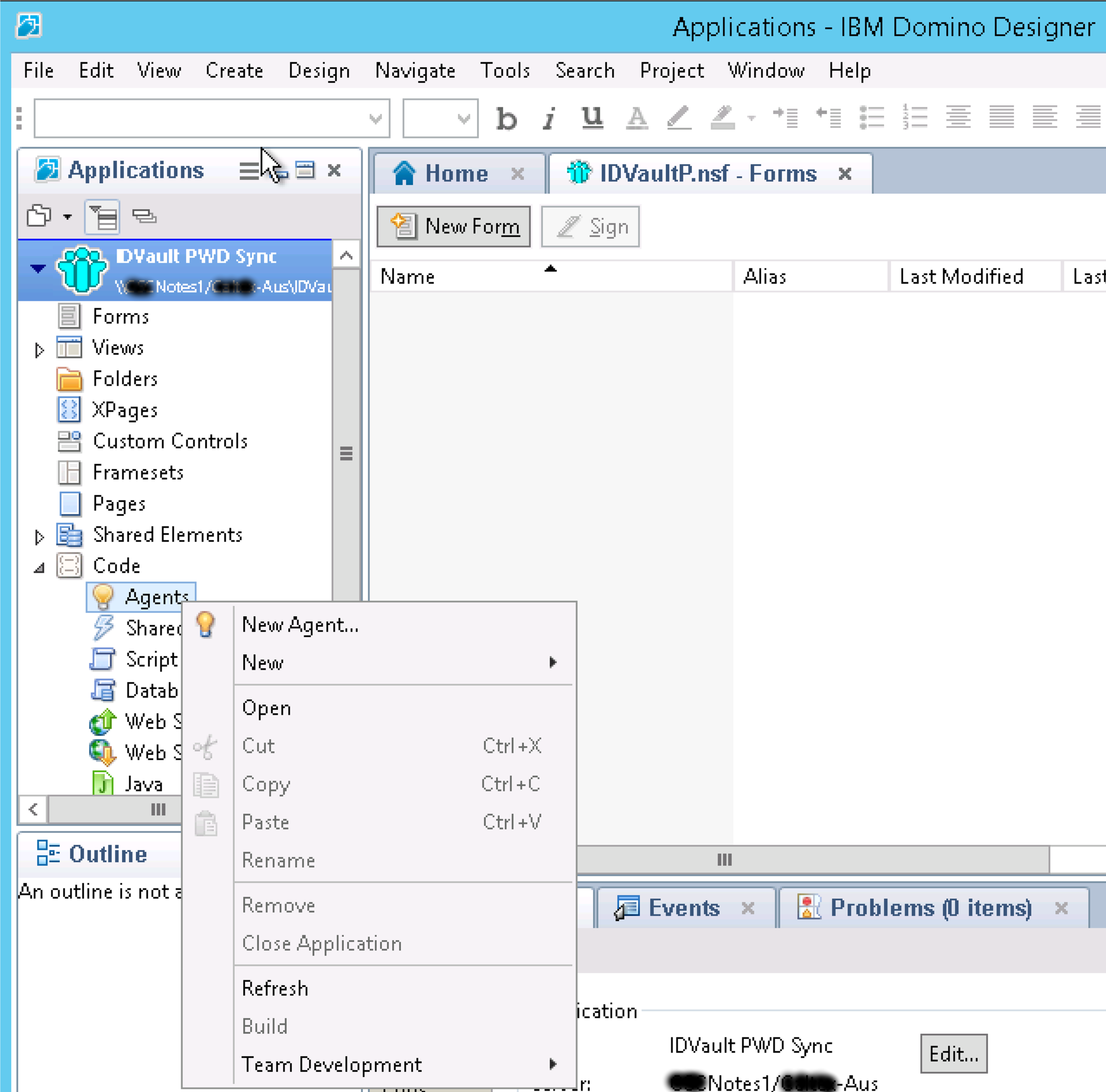
With the New Application created we can navigate to Code => Agents and select New Agent
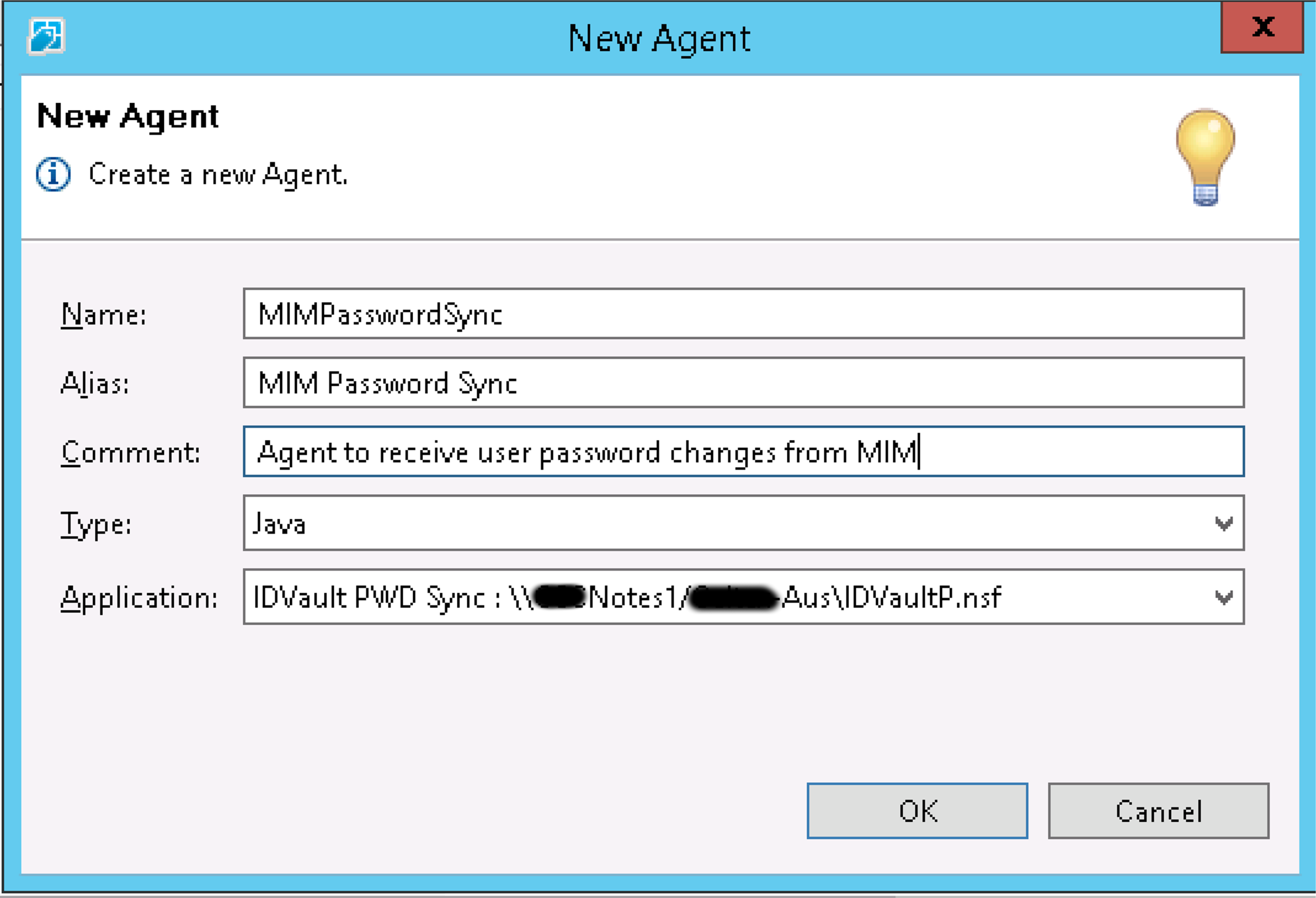
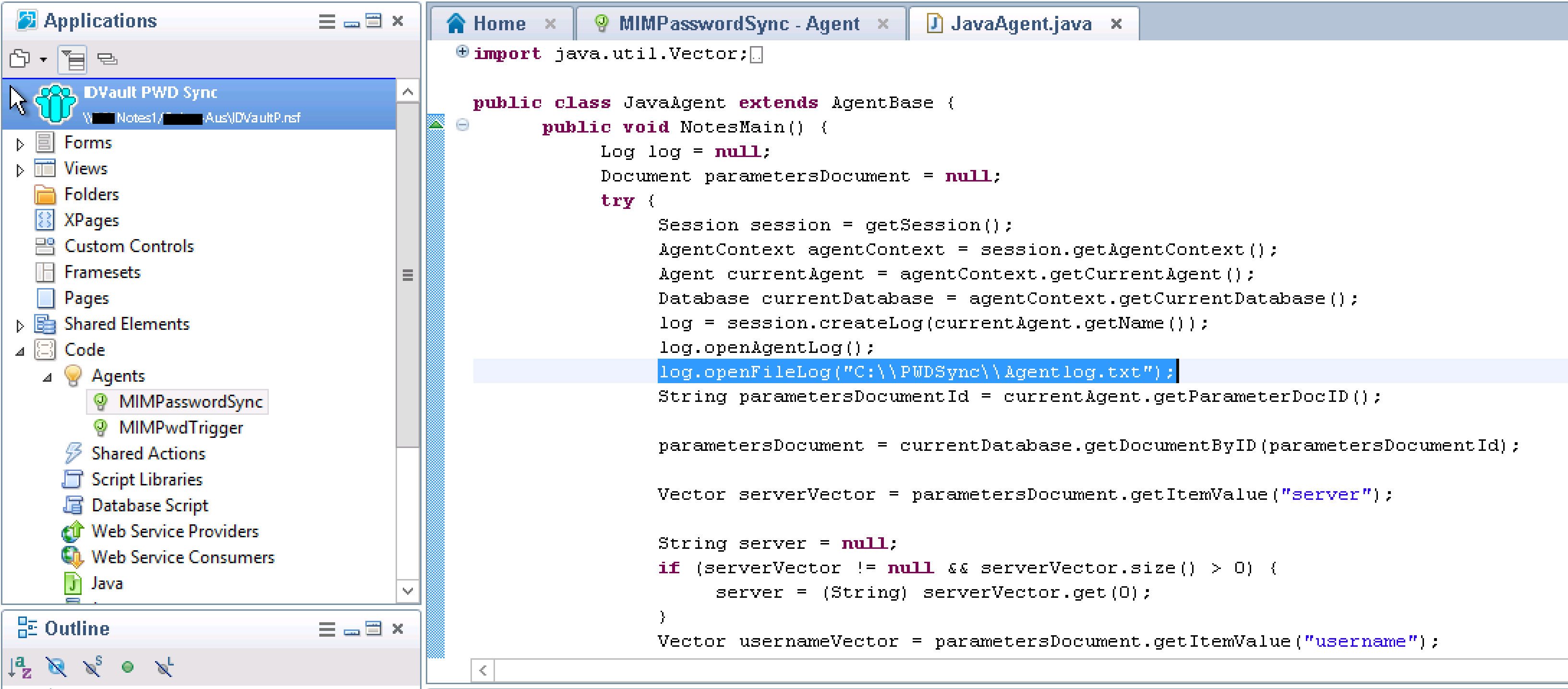
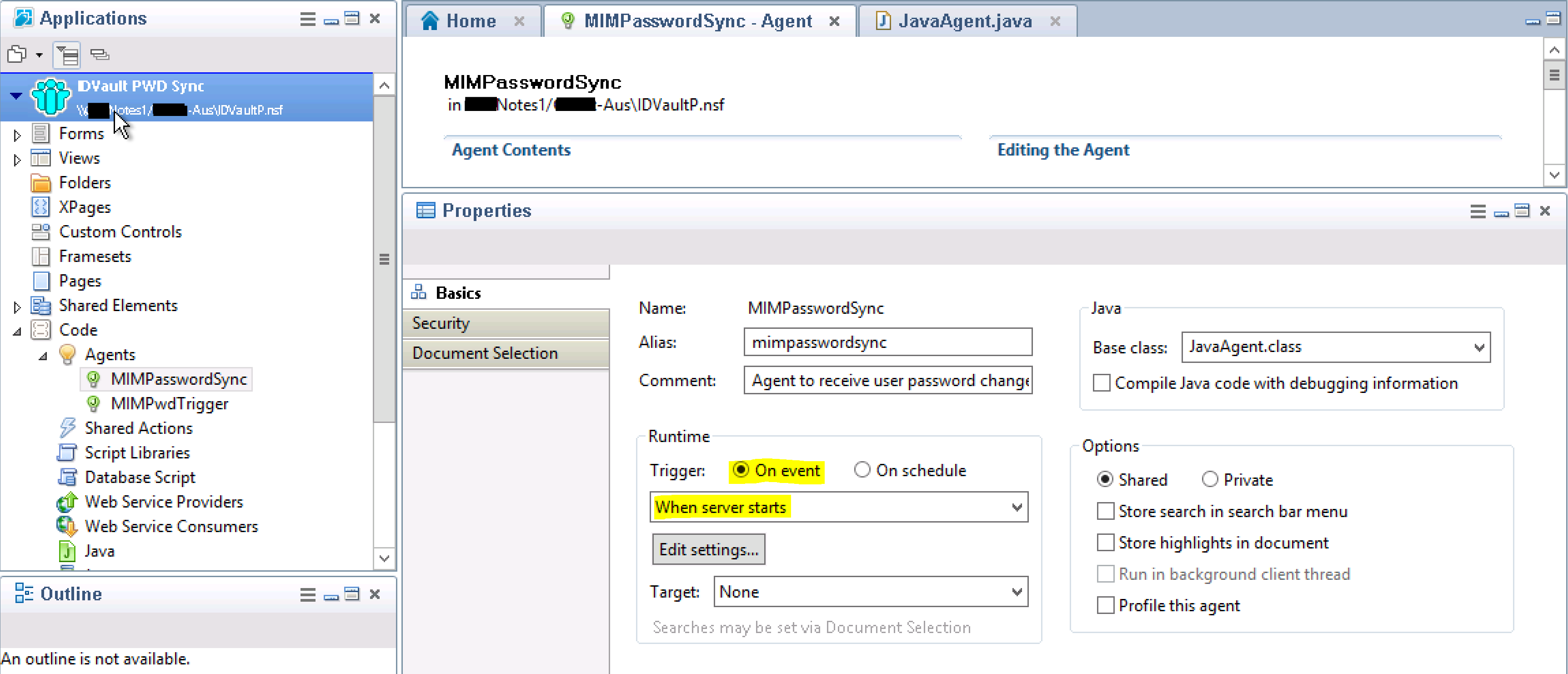
Give the Agent a name. I named this one MIMPasswordSync and make sure the type is Java
With the Agent created we need to give it the script that will perform the password changes. Double click on the agent then in the Agent Contents double-click on JavaAgent.java and paste in the script (from Github further below). The only change you may need to make is the location where you want the logging to go to. You will need to create that path if it doesn’t exist as well.
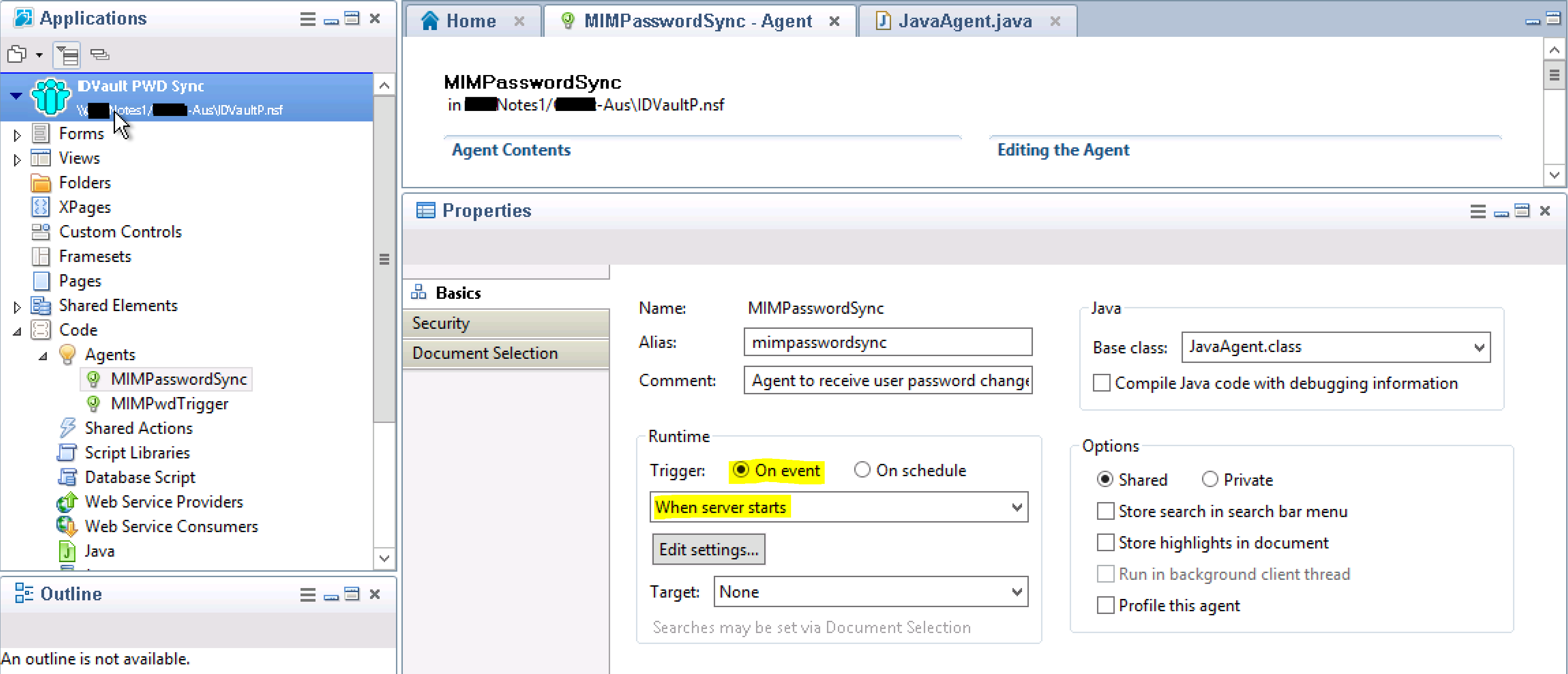
Selecting the Agent Tab in the main pain locate the Agent Properties and configure as per the screenshot below.
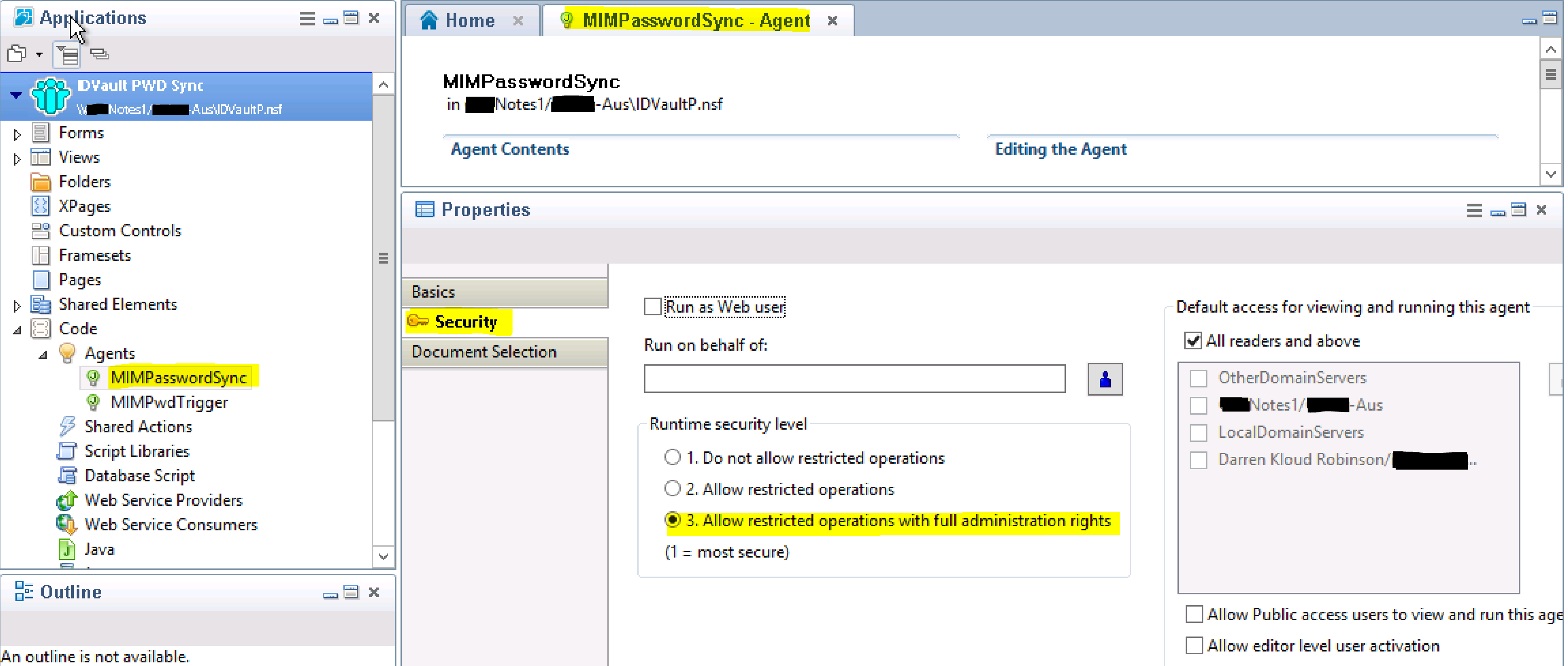
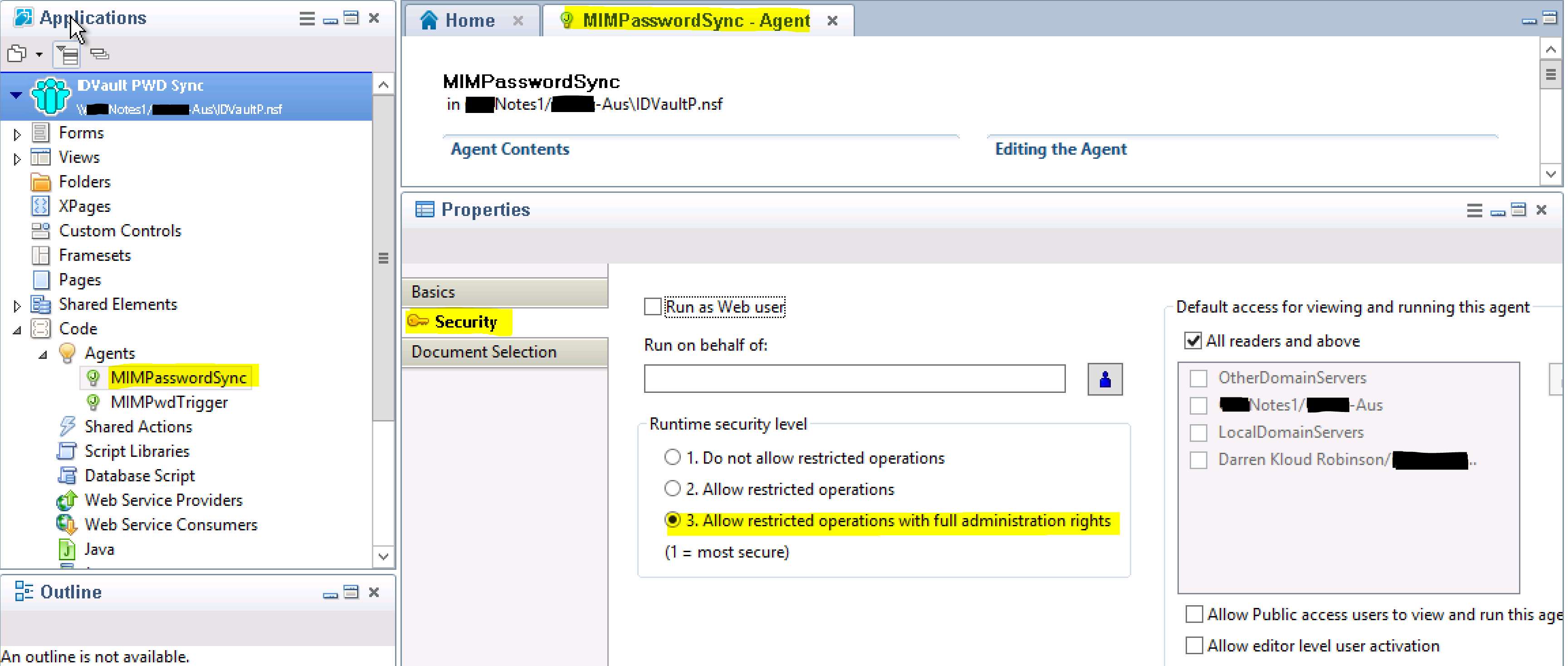
Select the Security Tab in the Properties pane and set the Runtime security level to 3. If the options are blanked out and you can’t select them, close the agent and re-open it and you will be able to configure this option.
Create the MIM Password Trigger Domino Agent
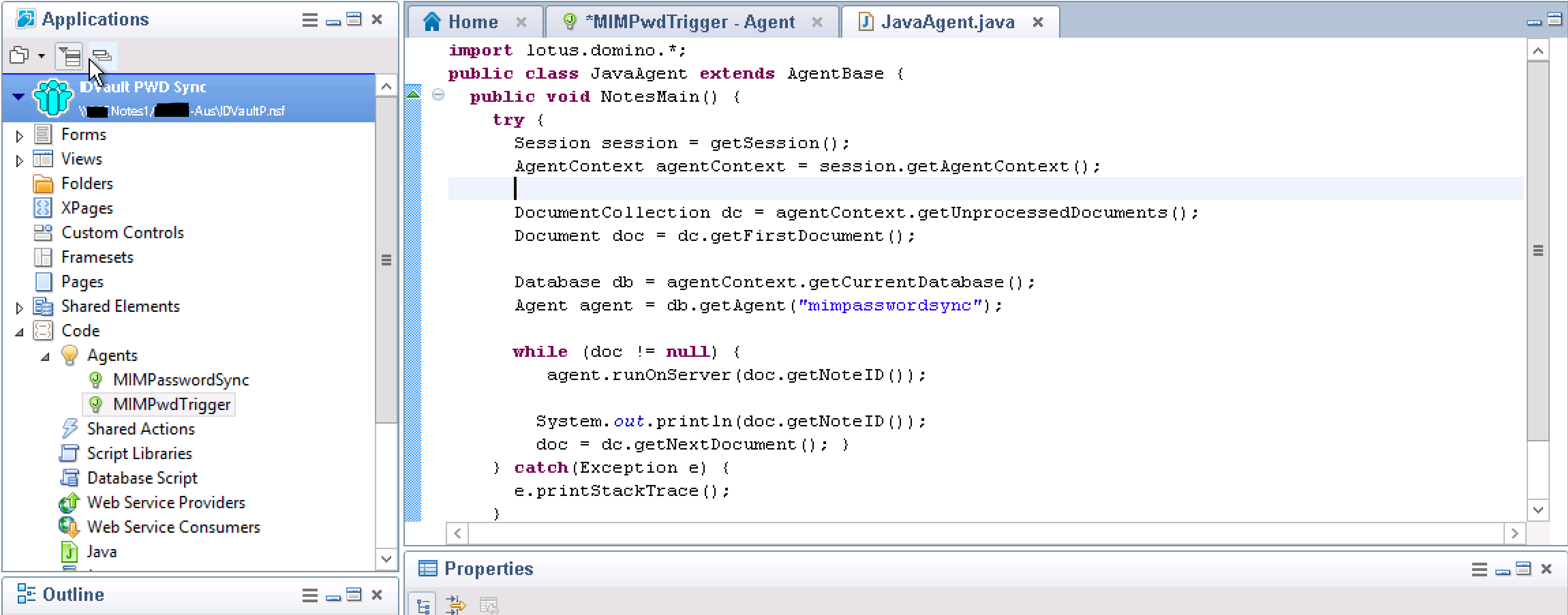
Create the MIM Password Trigger Domino Agent just as you did the MIM Password Sync Domino Agent. Name it MIMPwdTrigger and make sure the type is also Java. Double click on the Agent and then double-click on JavaAgent.java in the Agent Contents. Use the following script. Note it calls the MIMPasswordSync Agent so if you called yours something different you will need to change it in this script (line 12).
Select the MIMPwdTrigger Agent in the main pane and look at the Properties. Make Runtime to be On event and After documents are created or modified.
Select the Security Tab in the Properties pane and set the Runtime security level to 3. If the options are blanked out and you can’t select them, close the agent and re-open it and you will be able to configure this option
Configuration ID Vault Password Reset Authority
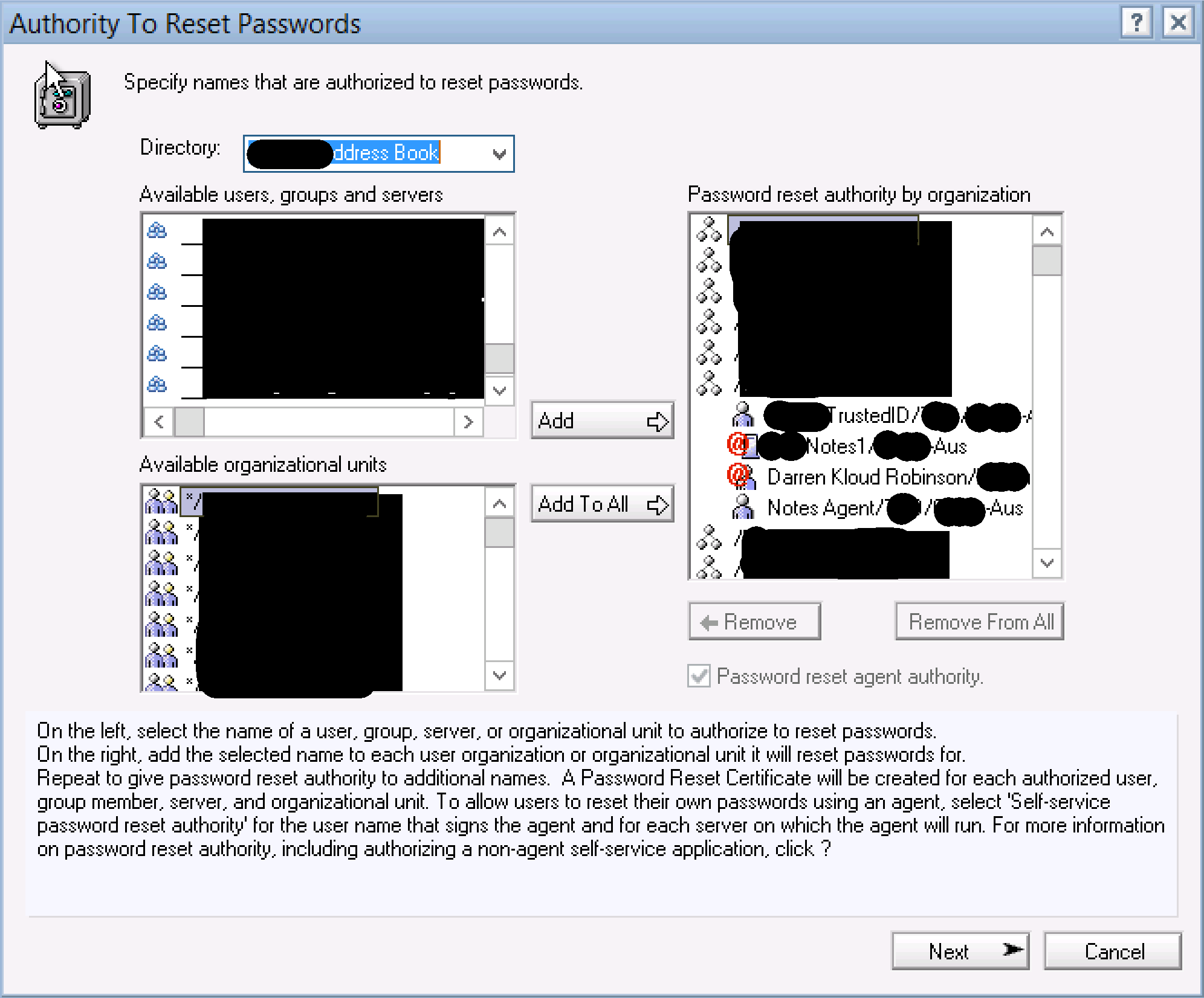
In order for our MIMPasswordSync Agent to actually change users passwords in the ID Vault we need to configure the ID Vault to allow the account that created and signs the Agents and the Server that the Agents will run on to be Trusted Password Reset Authorities.
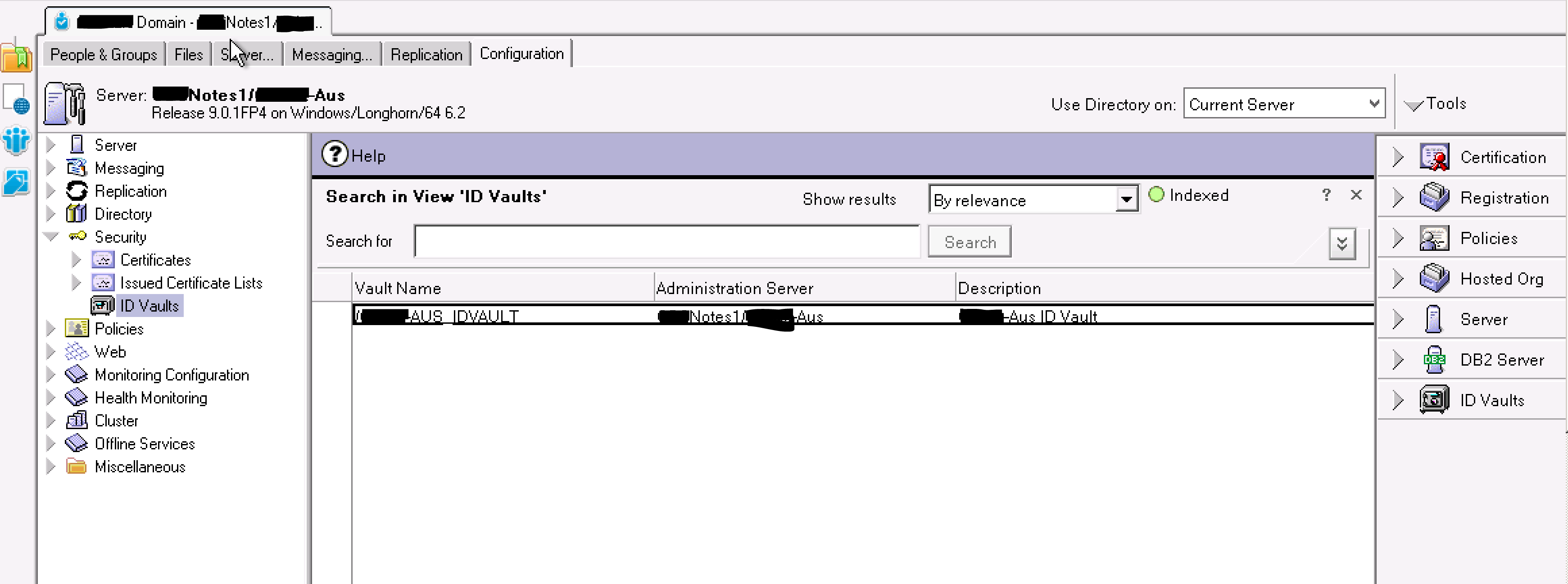
Using the IBM Domino Administrator select the Administration menu item and then Configuration. Expand Security from the left hand pane and select ID Vaults.
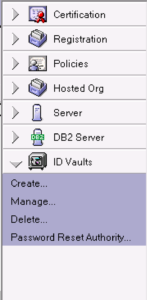
Having selected the ID Vault from the main pane you will be changing passwords in, on the right hand menu pane expand ID Vaults and double-click on Password Reset Authority.
From the Password reset authority by organisation box select the OrgU/Org you will be sync’ing passwords too. If you have many you will need to complete this step for each one. You will need to do one OrgU/Org at a time if they have different certifiers.
From the Available users, groups and servers box select the Server that you run the Agents with, and select Add. Repeat for selecting the user that you created the Agents with and that will sign the Agents. Then select the user you just added in the Password reset authority by organisation and then select the Password reset agent authority check box. That will put the red @ symbol on the user which identifies it as a Password Reset Agent Authority.
Select Next/Configure, locate the certifier ID for that OrgU/Org, provide the password and complete the process. Repeat for each OrgU/Org.
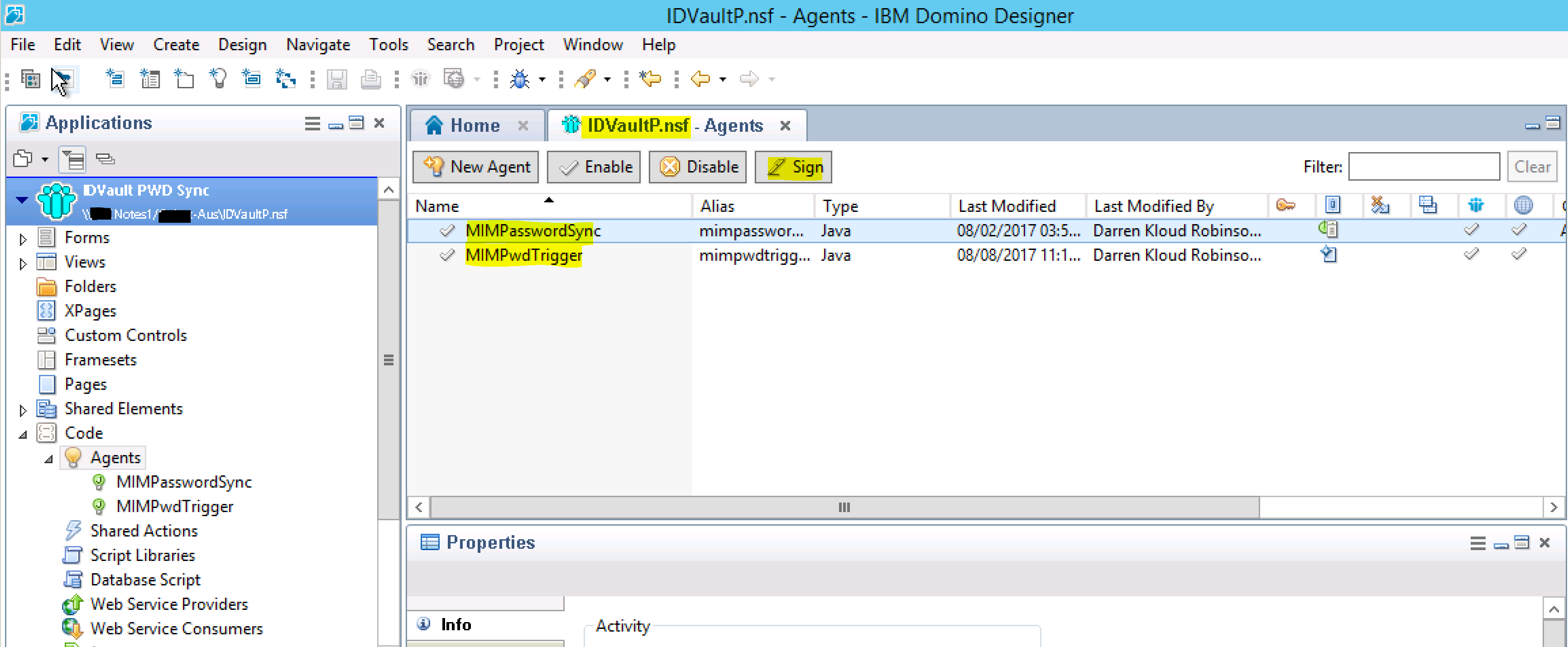
Signing the Agents
Back using the Domino Designer double-click Agents in the left menu pane. Select each Agent and then click Sign.
Creating a Form to test the Agents
Now we will create a form to allow us to create a document in the DB easily and test that our agents work. In Domino Designer, right-click on Forms and select New Form.
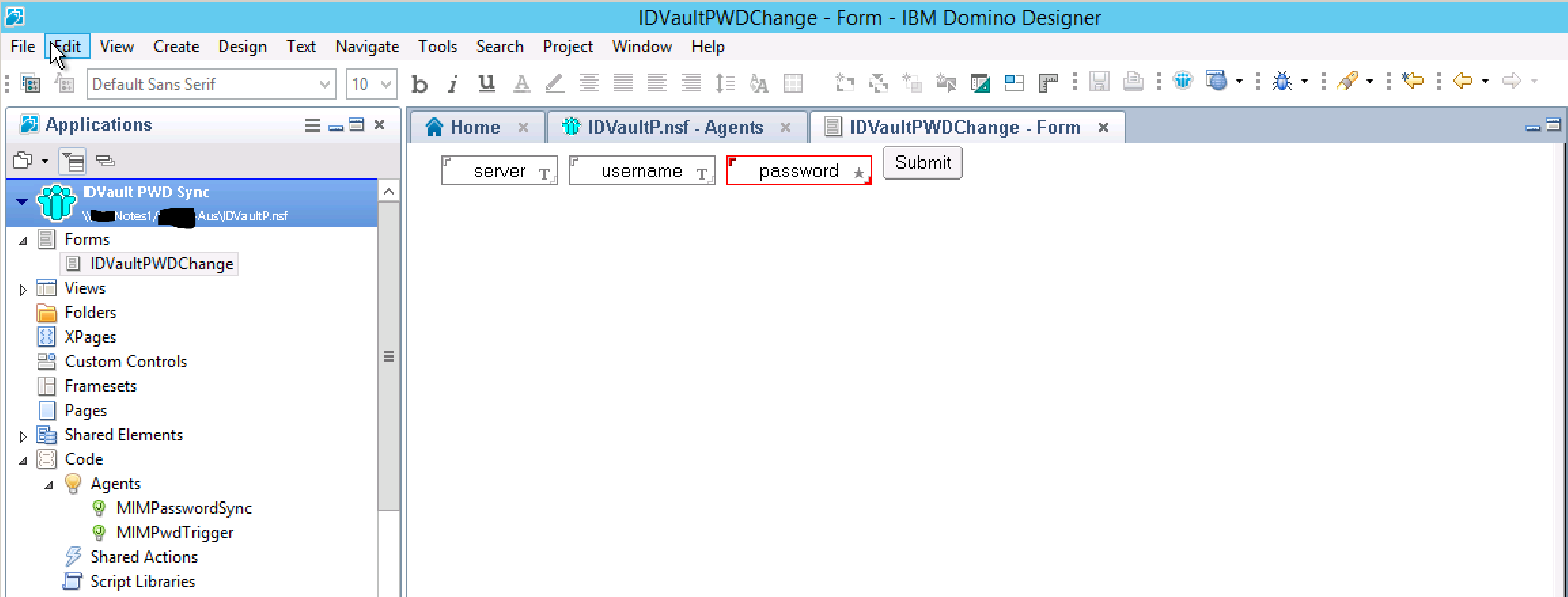
Give the Form a name and an alias. It doesn’t matter what you call it. We’re just using it to test the agents.
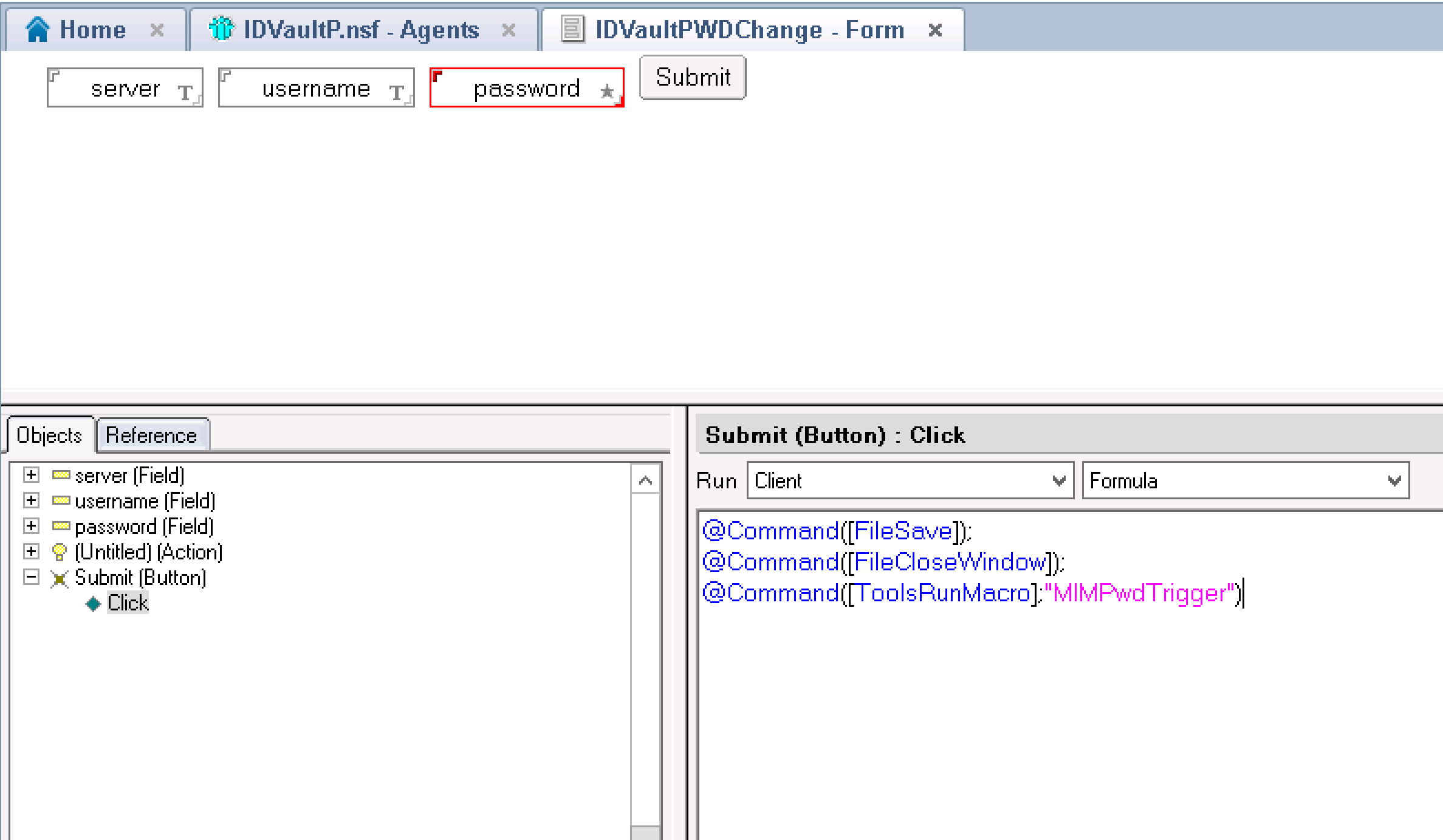
Double Click on your new Form. Click in the empty pane and then from the Create menu select Field. Name it server. Repeat for another field and name it username.
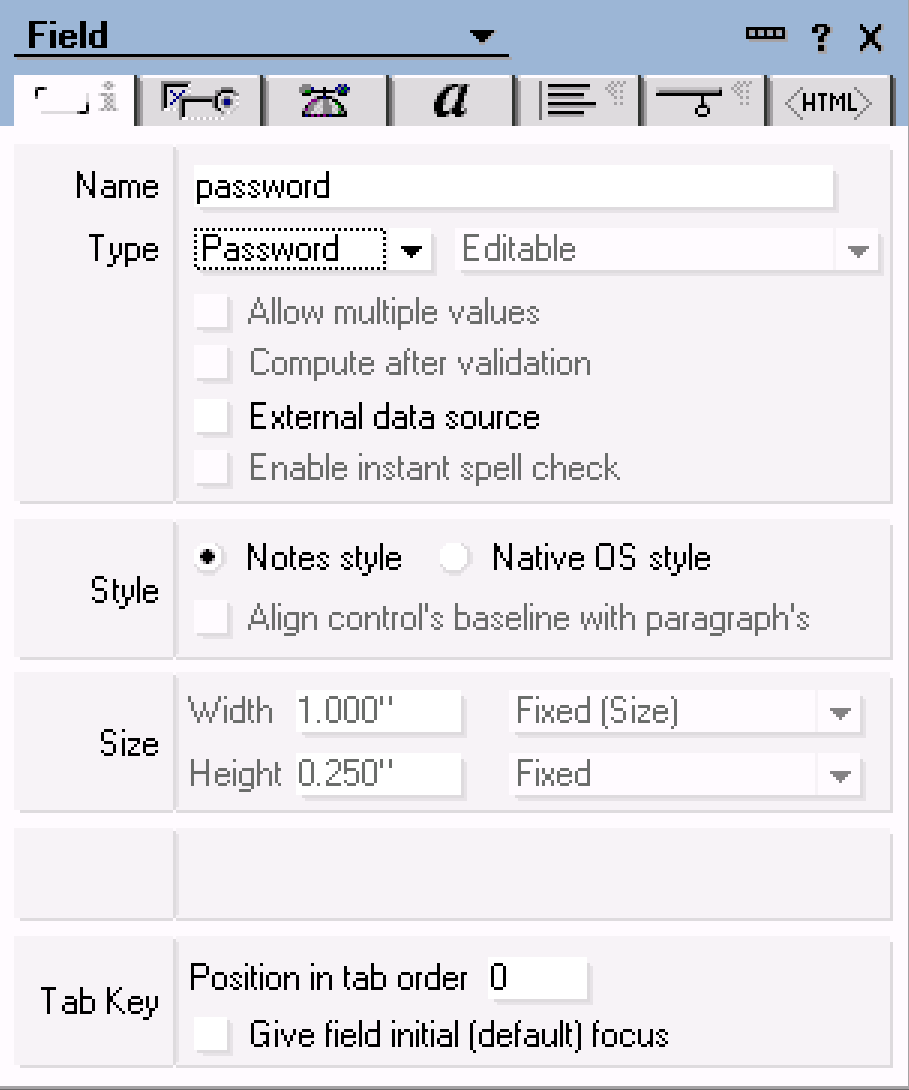
Repeat for the third text field, but name it password and select the Type Password.
Finally from the Create menu select Hotspot => Button. Name it Submit and then select it. In the Properties of the button for Run select Client. For Formula enter the formula below.
@Command([FileSave]); @Command([FileCloseWindow]); @Command([ToolsRunMacro];"MIMPwdTrigger")
Testing the Agents
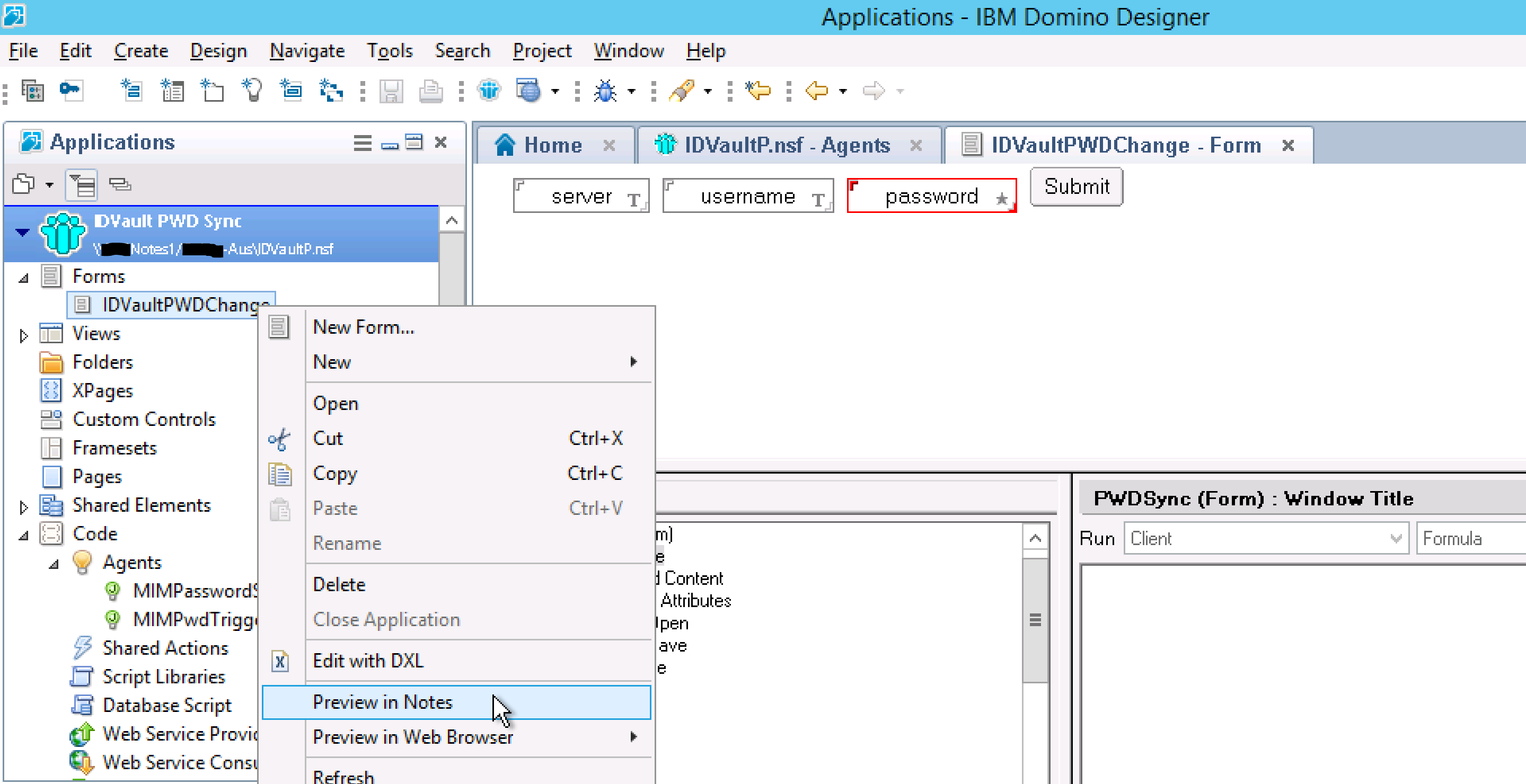
In the Domino Designer right-click on the form and select Preview in Notes.
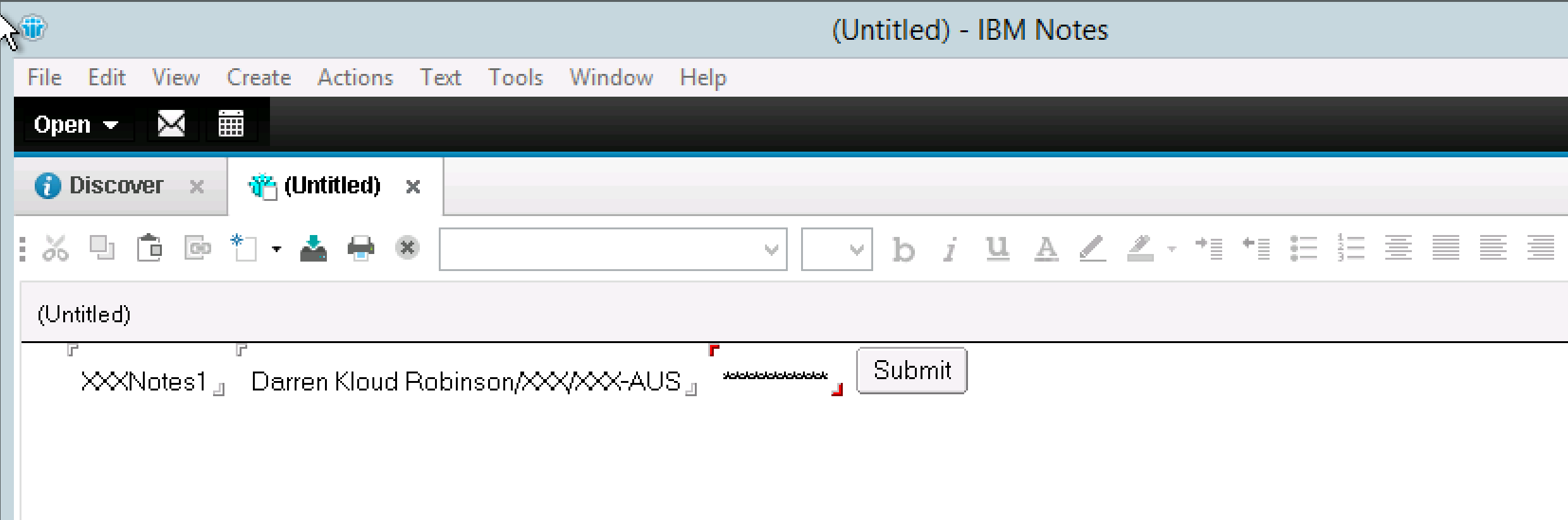
The format for the fields is;
- server: Server/Org
- user: Joe Smith/OrgU/Org
- password: P@SSw0rd
Enter valid input for your environment.
And click on the Submit button. If you have everything correct the document you just created will be processed by the Trigger Agent and then the MIM Password Sync Agent.
If there is an error you will likely have a document still in the IDVault PWD Sync database as shown below. Check the document to make sure you got the details for the user and server correct.
Also check the log file. C:\PWDSync\AgentLog.txt by default as per the script path. When working correctly you will see an entry as per below. If it wasn’t successful the error message should point you to where you have gone wrong. More than likely different names for the Agents, or incorrect format or name for the user and/or server. Or Trusted Password Authority not set for the account the agent was signed with to the OrgU/Org containing the user you are trying to change a password for.
MIMPasswordSync|mimpasswordsync: 08/08/2017 02:08:24 PM: Reseting password ... MIMPasswordSync|mimpasswordsync: 08/08/2017 02:08:24 PM: Server: XXXNotes1 User:Jane Doe/OrgU/Org-Aus MIMPasswordSync|mimpasswordsync: 08/08/2017 02:08:26 PM: Return value: true MIMPasswordSync|mimpasswordsync: 08/08/2017 02:08:26 PM: Removed User ID Vault change document from 'XXXNotes1'
Summary
Now that we have our Agents built and working we need to be able to call them from our MIM Sync Server. That will be covered in the third and final post in this series.