Recently I wrote about reporting on individual Azure AD Users Authentication Methods using Microsoft Graph and PowerShell. Whilst this is great at a user level, Azure AD Authentication Methods Summary Reports at an organization level are often requested by IT Management. And whilst they can be obtained from the Azure Portal (Azure Active Directory > Security > Authentication Methods > Activity) how can we get them programmatically? In this post l will show how to extract Azure AD Authentication Methods Summary Reports using Microsoft Graph and PowerShell.
Microsoft’s Authentication Methods Activity documentation shows what Azure AD Authentication Methods Summary Reports contain. The authentication methods usage reports provide visibility of how users in your organization use Azure Active Directory features such as Multi-Factor Authentication, Self-Service Password Reset and Passwordless authentication.
- How many users are registered for each authentication method
- How many users are registered for features such as Multi-Factor Authentication (MFA), Self-Service Password Reset (SSPR), and Passwordless authentication.
- The failure rates of each authentication method
Prerequisites
The example script in this post utilizes an additional PowerShell Module to simplify the process. You will require:
- MSAL.PS to simplify authentication to Microsoft Graph
- Install the module from the PS Gallery using PowerShell 5.1+ using command
- Install-Module MSAL.PS -Force -AcceptLicense
- Install the module from the PS Gallery using PowerShell 5.1+ using command
An Azure AD Tenant that is licensed for Azure AD Premium P1 or P2 in order to access usage and insights.
You will need to register an Azure AD Application with Delegated Permissions for the Reports.Read.All scope. The registered application will need to be authorized (Admin consent) for the tenant. The script will require the registered Application (client) ID and Directory (tenant) ID from the Overview page of the registered application.

When running the script for the first time it will initiate the DeviceCode flow (where you will go to https://microsoft.com/devicelogin and enter the code provided on the console output) and then sign-in with an Azure AD Account that must be a member of one of the following roles.
- Reports reader
- Security reader
- Security admin
- Global reader
- Global admin
Finally on the Authentication tab of your registered Azure AD Application you will need to enable “Allow public client flows” as shown below.

Script Functions
The script contains 5 functions. As mentioned above there is a function that leverages the MSAL.PS PowerShell Module to simplify authentication to Microsoft Graph. The DelegatedAuthN function takes the -clientID and -tenantID parameters. The ClientID is from the AAD registered application. The tenantID parameter is the objectID of the Azure AD Tenant where the application is registered.
The GetAADUsersAuthRegisteredByMethod function returns the summary of Azure AD Users’ Authentication registration methods.
The GetAADUsersAuthRegisteredByFeature function returns the summary of Azure AD Users’ Authentication registrations by feature.
The GetAADUsersCredentialUserRegistrationCount function returns the summary of Azure AD Users’ Registration Count by methods.
The GetAADUsersCredentialUsageSummary function returns the summary of Azure AD Users’ Credential method usage for Reset and Registration events.
Example Output
Here are examples of the output from each of the functions above.
Authentication Registrations by Method for Azure AD Users
$AuthRegisteredByMethod = GetAADUsersAuthRegisteredByMethod $AuthRegisteredByMethod.userRegistrationMethodCounts
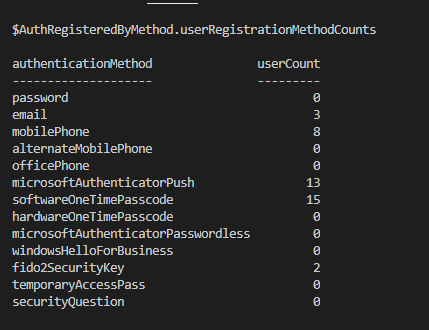
Authentication Registrations by Feature for Azure AD Users
$AuthRegisteredByFeature = GetAADUsersAuthRegisteredByFeature $AuthRegisteredByFeature$AuthRegisteredByFeature.userRegistrationFeatureCounts

Credential Registration Count for Azure AD Users
$CredentialUserRegistrationCount = GetAADUsersCredentialUserRegistrationCount $CredentialUserRegistrationCount $CredentialUserRegistrationCount.userRegistrationCounts

Credential Usage Summary for Azure AD Users
$CredentialUsageSummary = GetAADUsersCredentialUsageSummary -period '30' $CredentialUsageSummary

For each authentication method an object is returned for Reset and Registration events. Here is an example of the Reset use of the mobileSMS method. Note that GetAADUsersCredentialUsageSummary takes the -period parameter for the period (days) you are requesting a summary for. Valid options are 1, 7 and 30.

The Script
Below is the script with the functions to return the Azure AD Authentication Methods Summary Reports data.
The script is parameterized. Make the following updates with your configuration information;
- 188 for the Tenant ID that you will be retrieving the report from
- 190 for the ClientID of the registered Azure AD Application
- 194 only needs to be run once (per user profile on a machine) to authorize delegated access to the application. This will store an Access and Refresh token in the local MSAL Cache that can then be used to obtain new tokens.
Authorizing API Access
As mentioned above line 194 of the script only needs to be executed once (per user pofile on a local machine). It will output the following to the PowerShell console. Copy the URL to a browser and then use the one time code and then authenticate with an account for the Tenant associated with the TenantID and ClientID used that also has the permissions listed in the Prerequisites section.

Enter the Code from the console output above

Sign in with an account with the required permissions

If you’ve given the correct parameters with the appropriate access you will be successful in obtaining an Access Token with the necessary permissions.

Summary
It is awesome to see these features now in Microsoft Graph. Authentication Methods and their visibility was a shortcoming of Microsoft Graph for a long time.
The example script here can be extended to take the output and generate your own Microsoft Excel reports and charts (potentially inspired by what is available in the Azure Portal) using the ImportExcel PowerShell module that I showed in this recent post Getting Microsoft 365 Individual User Usage Reports with PowerShell.


