Reporting on users’ registered Azure AD Authentication methods is a more common request from enterprise security teams recently with the advance of Passwordless Authentication. In mid 2020 Microsoft added the ability to report on Azure AD Authentication Methods using Microsoft Graph, however ONLY with Delegated Microsoft Graph permissions. Finally, last month the ability to use Application permissions to query users’ Azure AD Authentication Methods using Microsoft Graph became available in the BETA API.
This post details using PowerShell to report on User Azure AD Authentication Methods using Microsoft Graph. Getting a users Azure AD Object and then updating it with their authenticationMethods will look like the screenshot below. I’ve added three additional attributes to the PSObject.
- AuthMethods which is the enrolled/configured AuthMethods for the user
- AuthMethodsDetails which is the detailed configuration for each AuthMethod
- AuthMethodsCount which is the number of enrolled/configured authentication methods for the user

There are numerous API’s associated with Authentication Methods. This post focuses on the enumeration of enrolled methods. Whilst each of the individual methods can also be queried independently (list phone methods, list email methods, list Windows Hello for Business methods, list Microsoft Authenticator Methods, list FIDO2 methods, list email methods and list password methods ), there is also the /beta/users/{objectID|UPN}/authentication/methods API that will return all enrolled methods for a user. That is the API that I’m using for this example.
Prerequisites
The example script in this post utilizes an additional PowerShell Module to simplify the process. You will require:
- MSAL.PS to simplify authentication to Microsoft Graph
- Install the module from the PS Gallery using PowerShell 5.1+ using command
- Install-Module MSAL.PS -Force -AcceptLicense
- Install the module from the PS Gallery using PowerShell 5.1+ using command
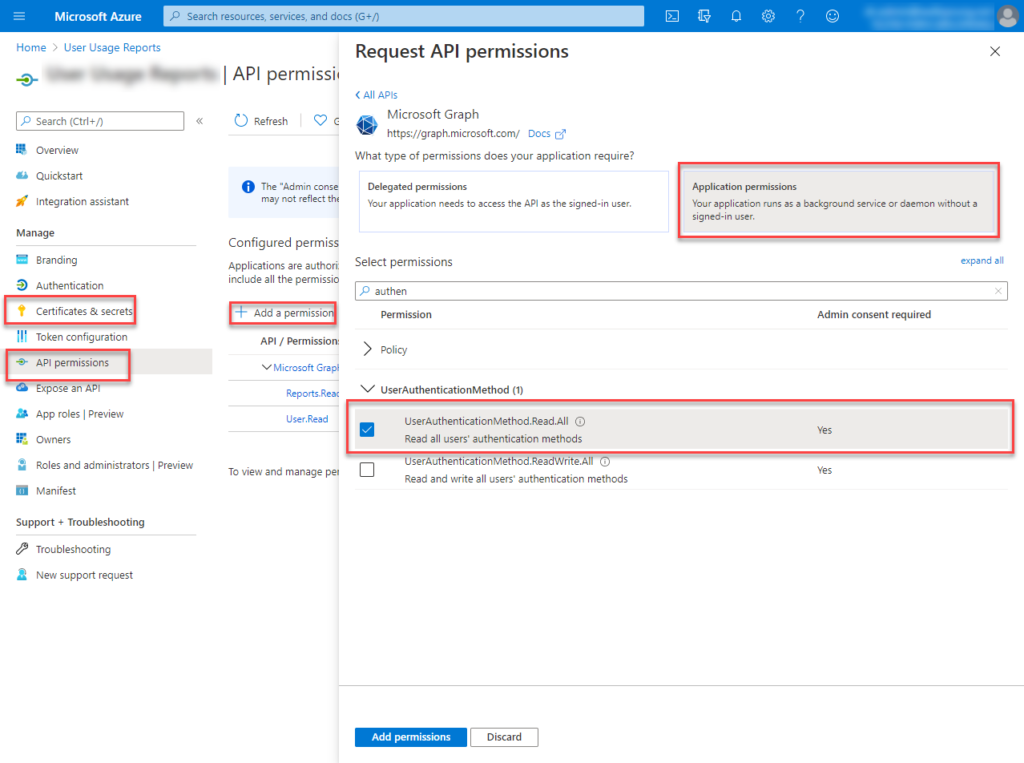
You will need to register an Azure AD Application with Application Permissions for the UserAuthenticationMethod.Read.All scope. If you don’t have a list of AAD user accounts you want to query you will need the User.Read.All scope too. The script example below uses both these scopes. The registered application will need to be authorized (Admin consent) for the tenant. You will need to record the registered Application (client) ID and Directory (tenant) ID from the Overview page of the registered application for use in the script. Finally, generate a secret from the Certificates & secrets tab and record the secret also for use in the script.
The Script
The script contains three functions. One to perform authentication to Microsoft Graph using the Tenant ID and Application (client) ID and Client Secret of the AAD Registered Application that contains UserAuthenticationMethod.Read.All and User.Read.All Application permissions, a function to obtain AzureAD Users’ and a function to get a user’s Authentication Methods.
As mentioned above there is a function that leverages the MSAL.PS PowerShell Module to simplify authentication to Microsoft Graph. The AuthN function takes the -credential and -tenantID parameters. The credential parameter is the ClientID and ClientSecret from the AAD registered application. The tenantID parameter is the objectID of the Azure AD Tenant where the application is registered.
The GetAADUsers function is used to get Azure AD Users’. It has an optional parameter (-limit) if you want to limit the returned users to a certain number, otherwise it will return all Azure AAD Users from the tenant.
Finally, the GetAuthMethods function will return the authentication methods for a user. It takes a single parameter (-UPN) which can be the UPN or the objectID of an Azure AD User.
The script is parameterized. Update the following lines with your configuration information that you recorded when you registered your AAD Application.
- 184 for the Tenant ID that you will be retrieving the report from
- 186 for the ClientID and ClientSecret of the registered Azure AD Application
Summary
Using the new authenticationMethods Microsoft Graph API we can return Azure AD user’s authentication method(s). The script then updates the local PowerShell Azure AD User Object to include the Authentication Methods for the user, the associated details of the authentication method(s) along with the number of authentication methods configured for the user. You can update the GetAADUsers function to include additional attributes if you want more than those returned by default.


