Updated: 28 May 2024 Module updated to v1.0.6 - Support for Linux (LF) line ending (previously the module only supported Windows (CRLF) - Code signed with updated cert - Updated with online code signing timestamp server Updated: 9 July 2020 – x.509 Certificate Details PowerShell Module updated to v1.0.5 - Code Signed - Fixes for PowerShell Core / PowerShell 7+
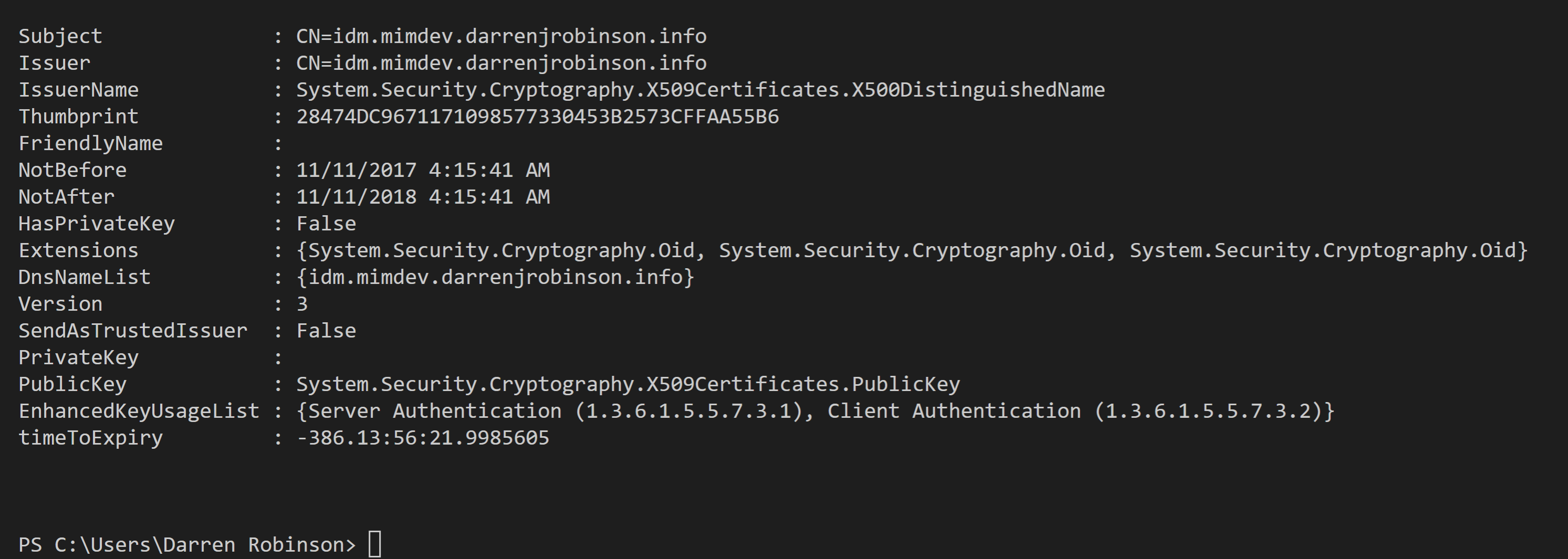
I’ve just published my X509 Certificate Details PowerShell Module to the PowerShell Gallery. The x.509 Certificate Details PowerShell Module contains the Get-X509Details cmdlet that decodes a base64 encoded PEM/CER format x.509 Certificate and converts it to a PowerShell Object. But wait, there’s more. The reason I created the x.509 Certificate Details PowerShell Module is because through automation I need to know what is the ‘Expiry Date’ for a certificate. The returned PowerShell Object from my Get-X509Details cmdlet in the X509Details Module also includes the expiry date-time in PowerShell DateTime format as ‘timeToExpiry‘. The inspiration for this module is from my JWTDetails PowerShell Module that I wrote recently and use extensively. It includes ‘expiryDateTime’ and ‘timeToExpiry’ fields in PowerShell DateTime format.
This means you can call the Get-X509Details cmdlet with a series of certificates and quickly inspect the ‘timeToExpiry‘ field to determine whether its time for you to go and generate a new certificate.
Installing the X509Details PowerShell Module
I’ve published the module to the PowerShell Gallery. Therefore with PowerShell Desktop 5.1 and later you can install direct from the PowerShell Gallery (in an Administrative PowerShell Session) using Install-Module.
Install-Module -name X509Details
Using Get-X509Details
Using Get-X509Details is super simple. Import the module and then pass it a base-64 encoded PEM/CER Certificate as per RFC 7468. The Get-X509Details cmdlet supports both the base-64 encoded certificate with and without the encapsulation boundaries (—–BEGIN CERTIFICATE—– and —–END CERTIFICATE—–) as described in RFC 4648.
Examples
Without encapsulation boundaries as a string.
Get-X509Details('MIIDtzCCAp+gAwIBAgIQZpJpy9zmR........URpc0T9DzsUUfoHfbQ==')
Using pipeline support as a string.
'MIIDtzCCAp+gAwIBAgIQZpJpy9zmR........URpc0T9DzsUUfoHfbQ==' | Get-X509Details
With encapsulation boundaries as a string.
Get-X509Details(@' -----BEGIN CERTIFICATE----- MIIDtzCCAp........URpc0T9DzsUUfoHfbQ== -----END CERTIFICATE----- '@)
Summary
I wrote this for myself for a bunch of automation I needed to do for directories full of certificates. It is very simplistic, but does what I needed it to do as part of larger scripts. Publishing it for myself and making it available in case its of use to anyone else. Source is on Github here.