Accessing Microsoft Office365, the Azure Portal, and the plethora of services we integrate with Azure Active Directory is for the most part seamless, especially when you only need to access a single tenant. However, it is 2021, and collaboration across tenants is the new normal. Personally, I have multiple browser profiles with each configured for differing tenants. For some applications such as Microsoft Teams you can use the tenant switcher, or in My Apps switch organizations. As administrators or enablers of services for end users it is often required that we provide customized links or QR Codes for Azure AD and Microsoft Office365 that contain deep link sign- in URLs that shows organizational branding and post login have the user defaulting to the correct tenant.
- In this post I detail
- Customized Azure AD Domain Name
- Deep Linking for Microsoft Office365 Applications (Teams, SharePoint, Outlook, Office Portal)
- Direct links for a tenants MyApps, MyAccess, MyAccount and MySignIns, Azure Self Service Password Reset
- Common / Well-Known ClientIDs for Microsoft Applications and Services
- Using PowerShell to generate QR Codes for Deep / Direct Links or B2B Self-Sign Up
Customized Azure AD Sign In Domain
The WHR (Windows Home Realm) parameter with Microsoft Office365 resources allows the branding and direct tenant sign-in to be shown. WHR is your Azure AD tenant.onmicrosoft.com or registered custom domain name address. (e.g., idmspecialist.com as shown below).
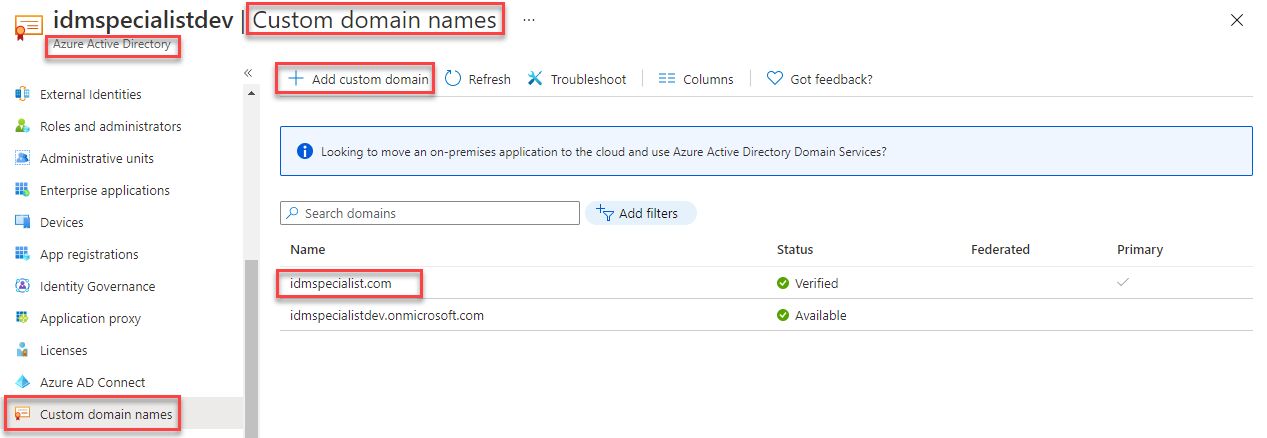
Using customized branding as I described in more depth in this post provides the ability to associate login with an organization immediately rather than after entering a user’s UPN.
Azure AD and Microsoft Office365 Deep Links
Microsoft Office365 Applications for a tenant can be directly accessed using the customized verified domain or the tenant.onmicrosoft.com address after the application address.
- Outlook
- outlook.com + tenant name | verified domain name
- https://outlook.com/idmspecialist.com
- outlook.com + tenant name | verified domain name
- Teams
- teams.microsoft.com + ?tenantId= + tenant name | verified domain name
- https://teams.microsoft.com/?tenantId=idmspecialist.com
- teams.microsoft.com + ?tenantId= + tenant name | verified domain name
- SharePoint
- tenant name + sharepoint.com
- https://idmspecialistdev.sharepoint.com
- tenant name + sharepoint.com
- Office Portal
- portal.office.com + ?tenantId= + tenant name | verified domain name
- https://portal.office.com/?tenantId=idmspecialist.com
- portal.office.com + ?tenantId= + tenant name | verified domain name
MyApps, MyAccess, MyAccount, MySignIns
- MyApps
- myapps.microsoft.com + tenant name | verified domain name
- http://myapps.microsoft.com/idmspecialist.com
- myapps.microsoft.com + tenant name | verified domain name
- MyAccess
- myprofile.microsoft.com + tenantId= + tenant name | verified domain name
- http://myprofile.microsoft.com/?tenantId=idmspecialist.com
- myprofile.microsoft.com + tenantId= + tenant name | verified domain name
- MyAccount
- myaccount.microsoft.com + tenantId= + tenant name | verified domain name
- https://myaccount.microsoft.com/?tenantId=idmspecialist.com
- myaccount.microsoft.com + tenantId= + tenant name | verified domain name
- MySignIns
- mysignins.microsoft.com + tenantId= + tenant name | verified domain name
- https://mysignins.microsoft.com/?tenantId=idmspecialist.com
- mysignins.microsoft.com + tenantId= + tenant name | verified domain name
Each of the above URLs are redirected for login using the branding for the specified Azure AD Tenant, rather than the common endpoint. The image below is an example displaying the customized branding as configured in this detailed post.

Azure AD Self Service Password Reset and Azure MFA Configuration
- Azure MFA
- account.activedirectory.windowsazure.com/proofup.aspx + ?whr= + tenant name | verified domain name
- https://account.activedirectory.windowsazure.com/proofup.aspx?whr=idmspecialist.com
- account.activedirectory.windowsazure.com/proofup.aspx + ?whr= + tenant name | verified domain name
- Azure SSPR
- passwordreset.microsoftonline.com + ?whr= + tenant name | verified domain name
- https://passwordreset.microsoftonline.com/?whr=idmspecialist.com
- passwordreset.microsoftonline.com + ?whr= + tenant name | verified domain name

Well-Known Client IDs
When you are trying to find a well-known ClientID for a Microsoft application or service it is often difficult. In the graphic two images above I was specifying the Azure AD Account for which the well-known ClientID is : 0000000c-0000-0000-c000-000000000000. Here is a list of well-known client ids.
"graph_api"= "1b730954-1685-4b74-9bfd-dac224a7b894" # MS Graph API
"aadrm"= "90f610bf-206d-4950-b61d-37fa6fd1b224" # AADRM
"exo"= "a0c73c16-a7e3-4564-9a95-2bdf47383716" # EXO Remote PowerShell
"skype"= "d924a533-3729-4708-b3e8-1d2445af35e3" # Skype
"www"= "00000006-0000-0ff1-ce00-000000000000" # Office portal
"o365spo"= "00000003-0000-0ff1-ce00-000000000000" # SharePoint Online
"o365exo"= "00000002-0000-0ff1-ce00-000000000000" # Exchange Online
"dynamicscrm"= "00000007-0000-0000-c000-000000000000" # Dynamics CRM
"o365suiteux"= "4345a7b9-9a63-4910-a426-35363201d503" # O365 Suite UX
"aadsync"= "cb1056e2-e479-49de-ae31-7812af012ed8" # Azure AD Sync
"aadconnectv2"= "6eb59a73-39b2-4c23-a70f-e2e3ce8965b1" # AAD Connect v2
"synccli"= "1651564e-7ce4-4d99-88be-0a65050d8dc3" # Sync client
"azureadmin" = "c44b4083-3bb0-49c1-b47d-974e53cbdf3c" # Azure Admin web ui
"pta" = "cb1056e2-e479-49de-ae31-7812af012ed8" # Pass-through authentication
"patnerdashboard" = "4990cffe-04e8-4e8b-808a-1175604b879" # Partner dashboard (missing on letter?)
"webshellsuite" = "89bee1f7-5e6e-4d8a-9f3d-ecd601259da7" # Office365 Shell WCSS-Client
"teams" = "1fec8e78-bce4-4aaf-ab1b-5451cc387264" # Teams
"office" = "d3590ed6-52b3-4102-aeff-aad2292ab01c" # Office, ref. https://docs.microsoft.com/en-us/office/dev/add-ins/develop/register-sso-add-in-aad-v2
"office_online2" = "57fb890c-0dab-4253-a5e0-7188c88b2bb4" # SharePoint Online Client
"office_online" = "bc59ab01-8403-45c6-8796-ac3ef710b3e3" # Outlook Online Add-in App
"powerbi_contentpack" = "2a0c3efa-ba54-4e55-bdc0-770f9e39e9ee" # PowerBI content pack
"aad_account" = "0000000c-0000-0000-c000-000000000000" # https://account.activedirectory.windowsazure.com
"sara" = "d3590ed6-52b3-4102-aeff-aad2292ab01c" # Microsoft Support and Recovery Assistant (SARA)
"office_mgmt" = "389b1b32-b5d5-43b2-bddc-84ce938d6737" # Office Management API Editor https://manage.office.com
"onedrive" = "ab9b8c07-8f02-4f72-87fa-80105867a763" # OneDrive Sync Engine
"adibizaux" = "74658136-14ec-4630-ad9b-26e160ff0fc6" # Azure portal UI "ADIbizaUX"
"msmamservice" = "27922004-5251-4030-b22d-91ecd9a37ea4" # MS MAM Service API
"teamswebclient" = "5e3ce6c0-2b1f-4285-8d4b-75ee78787346" # Teams web client
"azuregraphclientint" = "7492bca1-9461-4d94-8eb8-c17896c61205" # Microsoft Azure Graph Client Library 2.1.9 Internal
"azure_mgmt" = "84070985-06ea-473d-82fe-eb82b4011c9d" # Windows Azure Service Management API
"az" = "1950a258-227b-4e31-a9cf-717495945fc2" # AZ PowerShell Module
"f8d98a96-0999-43f5-8af3-69971c7bb423" # Apple Internet Accounts
"7f59a773-2eaf-429c-a059-50fc5bb28b44" # https://docs.microsoft.com/en-us/rest/api/authorization/globaladministrator/elevateaccess#code-try-0
"9bc3ab49-b65d-410a-85ad-de819febfddc" # SPO Management Shell
"06c6433f-4fb8-4670-b2cd-408938296b8e" # AAD Pin redemption client
"19db86c3-b2b9-44cc-b339-36da233a3be2" # https://mysignins.microsoft.com
"00b41c95-dab0-4487-9791-b9d2c32c80f2" # Office 365 Management (mobile app)
"29d9ed98-a469-4536-ade2-f981bc1d605e" # Microsoft Authentication Broker (Azure MDM client)
"6f7e0f60-9401-4f5b-98e2-cf15bd5fd5e3" # Microsoft.AAD.BrokerPlugin resource:https://cs.dds.microsoft.com
"38aa3b87-a06d-4817-b275–7a316988d93b" # Microsoft AAD Cloud AP
"0c1307d4-29d6-4389-a11c-5cbe7f65d7fa" # Azure Android App
"6c7e8096-f593-4d72-807f-a5f86dcc9c77" # Intune MAM client resource:https://intunemam.microsoftonline.com
"4813382a-8fa7-425e-ab75-3b753aab3abb" # Authenticator App resource:ff9ebd75-fe62-434a-a6ce-b3f0a8592eaf
"1fec8e78-bce4-4aaf-ab1b-5451cc387264" # Teams client
"de0853a1-ab20-47bd-990b-71ad5077ac7b" # Windows Configuration Designer (WCD)
"b90d5b8f-5503-4153-b545-b31cecfaece2" # AADJ CSPSee the deep links with QR Codes section below for using Azure AD registered applications with deep linking. But for Microsoft applications and services their well-known client IDs can be used for deep links too.
Logout
Sometimes you end up in a loop with authentication to too many tenants cached in a browser (or connected accounts in your profile) and no matter how much you try and direct yourself to the right place, you keep getting bounced to another tenant.
The only course of action here is to sign out of the tenant you are unintentionally being bounced too. This is the link you need. Select the identity associated with the tenant you are being bounced to, to logout from.
https://login.microsoftonline.com/logout.srf
Direct / Deep Links with QR Codes
Let’s say you have an Azure AD registered Application that you want to make available outside your organization and allow Self Service Sign Up for. That is possible using External Identities detailed here. With that all configured and the application enabled for self-service sign-up, you will want to provide a link to those external users to allow them to self-sign up. The sign-up sign in URL is comprised of:
- Azure AD oAuth2 Authorization endpoint associated with the AAD Domain so that the configured branding is shown (here idmspecialist.com)
- https://login.microsoftonline.com/idmspecialist.com/oauth2/v2.0/authorize
- Client (Application) ID of the Azure AD registered Application
- client_id=7ad7a397-3670-4961-8acf-123456789abc
- Domain Hint for branding configuration
- domain_hint=idmspecialist.com
- Response Type to trigger the redirect
- response_type=id_token
- The minimalist default (delegated) scope for AuthN to work
- scope=https://graph.microsoft.com/user.read
After Sign Up, if you have a landing page or a method to identify the users account name you can also provide that as part of the login URL and the user will be directed to provide their password. For that you pass.
- Login Hint with the users account address
- login_hint=username@idmspecialist.com
On your AAD Registered Application ensure that you have ID tokens selected on the Authentication page.

All put together that looks like this.
https://login.microsoftonline.com/idmspecialist.com/oauth2/v2.0/authorize?client_id=7ad7a397-3670-4961-8acf-123456789abc&domain_hint=idmspecialist.com&response_type=id_token&scope=https://graph.microsoft.com/user.read
You could send that out as a hyperlink in an email, but also as a QR Code. Using the QRCodeGenerator PowerShell Module and the New-PSOneQRCodeURI cmdlet we can generate a QR Code using PowerShell.
Import-Module QRCodeGenerator New-PSOneQRCodeURI -URI "https://login.microsoftonline.com/idmspecialist.com/oauth2/v2.0/authorize?client_id=7ad7a397-3670-4961-8acf-123456789abc&domain_hint=idmspecialist.com&response_type=id_token&scope=https://graph.microsoft.com/user.read" -Width 50 -OutPath "$home\Desktop\AADSignUpQR.png" -Show

Summary
Over time I’ve had to lookup or workout the syntax for the differing services in order to get the right Azure AD and Microsoft Office365 deep links. In this post I’ve tried to summarize them, so if even only for me the next time I need one I can find it quicker.


