Installing and configuring a SailPoint IdentityNow RACF Connector isn’t something you do everyday. It’s probably something you will only over do once or twice it at all. This post is my learnings from troubleshooting the SailPoint IdentityNow RACF Connector Gateway to allow the IdentityNow RACF Source to connect to the RACF Agent on z/OS. The best background reference for such a configuration is this document on Compass. The IdentityNow RACF Connector Gateway can be downloaded from here.
UPDATE: July 2019 - There is an updated Windows Connector Gateway version available from here
Prerequisites
- Java Development Kit 1.8 (32-bit and 64-bit) or later is required
Connector Gateway
The SailPoint documentation details extracting the connector gateway client to a temporary location. Then edit the install.bat for the JDK location and run install.bat 64 (for the 64-bit version). However the installation will actually install and configure the Connector Gateway Service using the binaries from wherever you are running the installation from. So locate the Connector Gateway executables in the location where you want them to reside. Then run install.bat 32|64
RACF Agent Port
The Port you configure in your init.xml configuration file isn’t the only port you will need to have open for the Connector Gateway to connect to the RACF Agent. Below shows my configuration for port 2470.
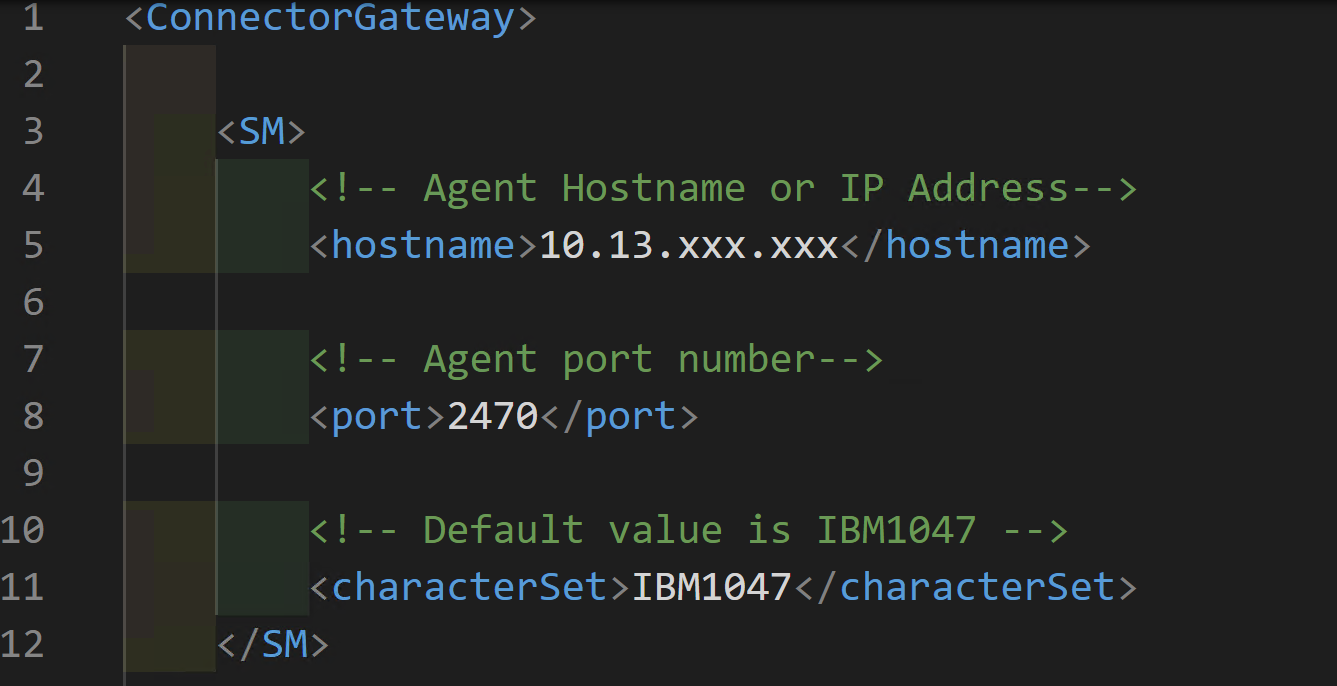
Yet the Connector Gateway was timing out. Wireshark shows that even though Port 2470 is configured I also needed Port 2471.

Opening up that port showed communications flowing and looking in the connector_gateway.log file under the log directory where the Connector Gateway is running showed a successful connection.
2019-06-25 15:51:40,818 INFO main sailpoint.router.sm.SMConnection:290 - Retrying to connect to Agent... 2019-06-25 15:51:49,818 INFO main sailpoint.router.common.Main:96 - 2019/06/25 15:51:49 Connected to Agent. 2019-06-25 15:51:49,818 INFO main sailpoint.router.common.Main:103 - 2019/06/25 15:51:49 Connector Gateway initialized successfully. 2019-06-25 15:51:49,818 INFO main sailpoint.router.common.Main:105 - 2019/06/25 15:51:49 TLSParameters enableCGtoPE2TLS false | enableCGtoAgentTLS false
Connector Gateway Incoming Port
Chances are you are running the Connector Gateway on a Windows Host, that should by default have a Firewall enabled. When testing connectivity from the IdentityNow RACF Source in the IdentityNow Portal you will probably get the following error.
java.lang.InterruptedException: Timeout waiting for response to message 2 from client 66670afc-4dd6-483d-a99d-b76b3bca3e49 after 15 seconds.
![]()
You will need to allow the port you have configured your Connector Gateway for to pass traffic in. On the Windows Host running the Connector Gateway using an Administrator PowerShell session run the following command;
New-NetFirewallRule -Name "Allow IdentityNow Virtual Appliances" -DisplayName 'Allow from VANETWORKNAME' -Enabled True -Direction Inbound -Protocol ANY -Action Allow -Profile ANY -RemoteAddress VAIPADDRESS|CIDRofVANet
e.g
New-NetFirewallRule -Name "Allow IdentityNow Virtual Appliances" -DisplayName 'Allow from 10.12.13.0/26' -Enabled True -Direction Inbound -Protocol ANY -Action Allow -Profile ANY -RemoteAddress 10.12.13.0/26
Using Wireshark you will then be able to see the incoming traffic from the Virtual Appliance to the host with the Connector Gateway installed.
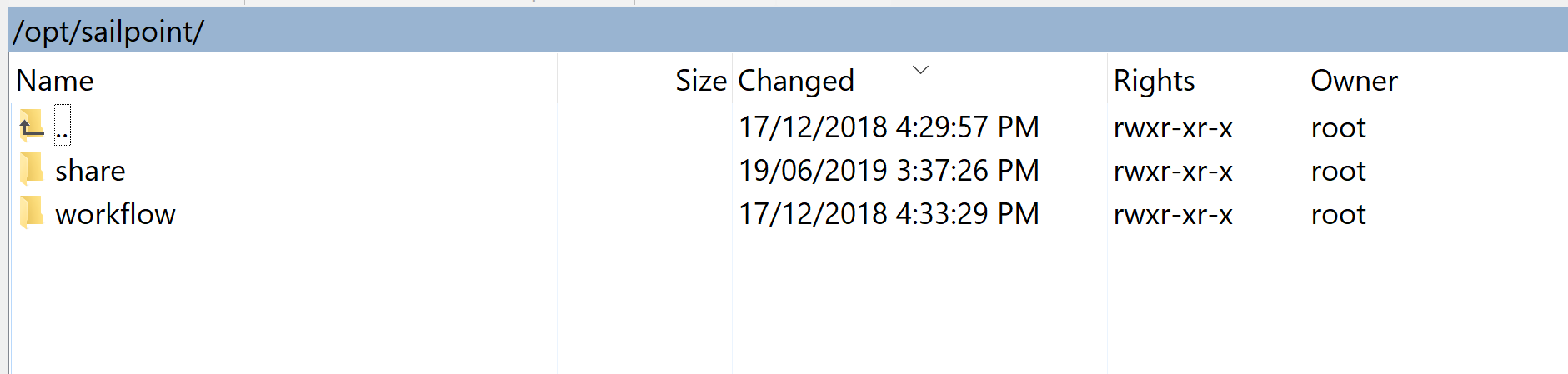
Test Connection – deskey.dat does not exists (sp?)
Testing the connection again may give you the following error.
The encryption key file /opt/sailpoint/ccg/lib/custom/deskey.dat does not exists. Please check the file name
![]()
Looking for that file and folder on the VA confirmed that it was not present (or a Non-SailPoint Services login to the VA does not have access).
Looking at the configuration of the RACF Source via the API showed the parameter.
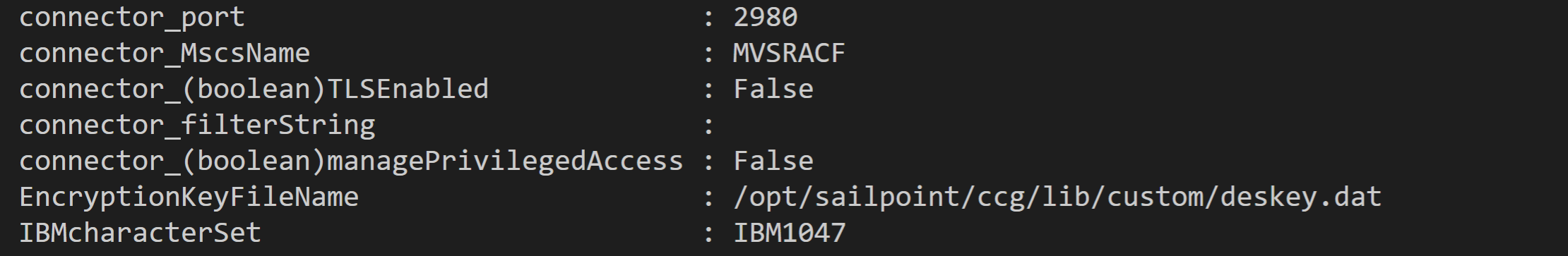
However, what this ACTUALLY means is that the Mainframe Operators have installed and configured the z/OS Agent on the RACF Host with Transmitted Data Encryption enabled.
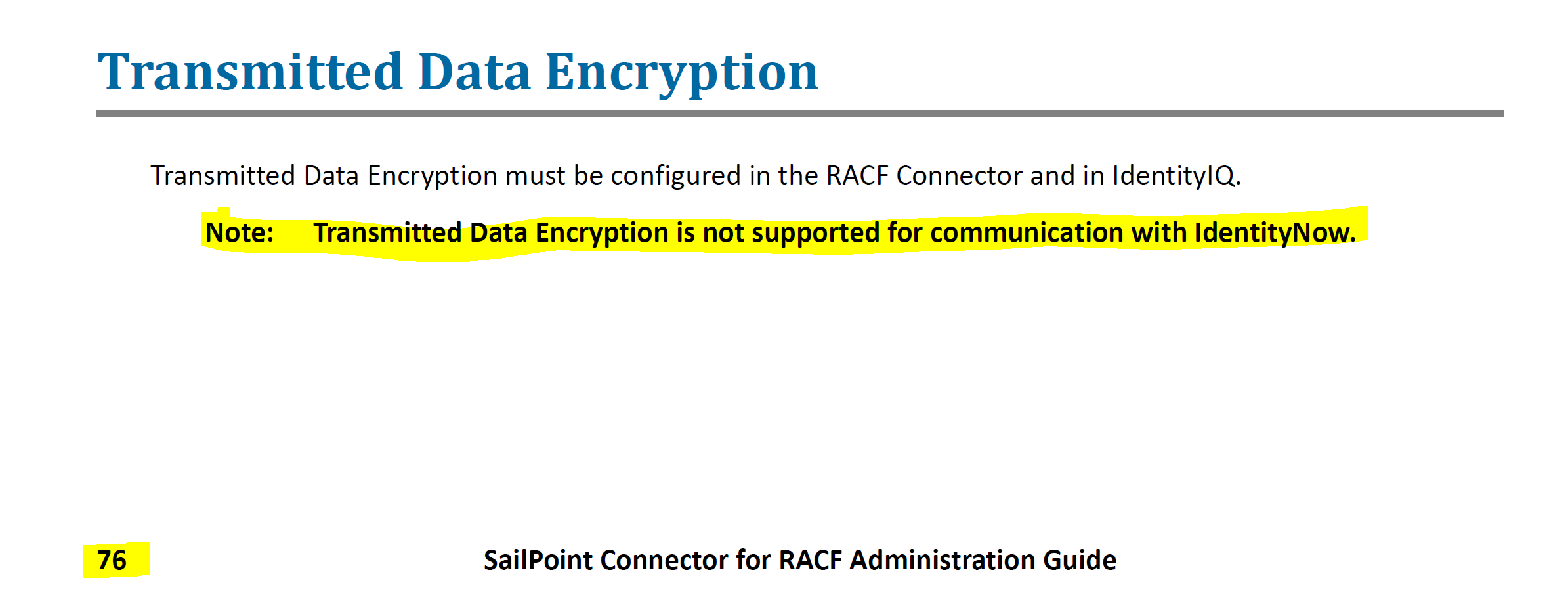
RACF Transmitted Data Encryption
From Page 76 of the 4_0_01_SailPoint_Connector_for_RACF_Admin_Guide.pdf document you will find this. Transmitted Data Encryption is not a supported configuration for use with IdentityNow.
You will need to get your Mainframe Operators to remove Transmitted Data Encryption and then you will be able to Test Connectivity and you should see;
Summary
The key to getting IdentityNow configured with a RACF Source is the correct configuration and network connectivity. Hopefully my experience and learnings help you get up and running quicker.